442 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
Deployment overview
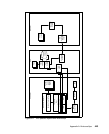
The solution deployment starts with the registration of a set of attributes for the
IBM Integrated Security Solution for Cisco Networks on the Cisco Secure ACS
server, as shown in Figure A-1 on page 443. This registration describes the type
of data that will be passed to the ACS by the Tivoli Compliance and Remediation
subsystems. Currently. two IBM attributes are registered with ACS:
PolicyVersion and ViolationCount.
Next, a policy is installed on the client. This policy is created on the Security
Compliance Manager server but for the purposes of troubleshooting, this is
transparent to the client. It is the installed
policy on the client that is of interest.
Note that when a new policy is installed a new set of
collector objects will be
placed in the%SCM_HOME%/.client/collectors directory. These collectors
determine what data the client will collect.
The Configuration Manager server is also loaded with
remediation (or software)
artifacts
, which are the objects of code that will be used to effect remediation on
the clients. Examples of these artifacts would be self-installing updates, updated
definition files, updated policy files, and so on.
After the solution has been configured with these objects, the NAC process is
started. The following sequence diagrams provide a detailed description of the
timing and events that happen during a typical NAC admission procedure.
In Figure A-1 on page 443, the shadowed boxes represent files or content that is
imported or modified to change the behavior of the deployment. The heavily lined
boxes represent software that is installed as part of the deployment.