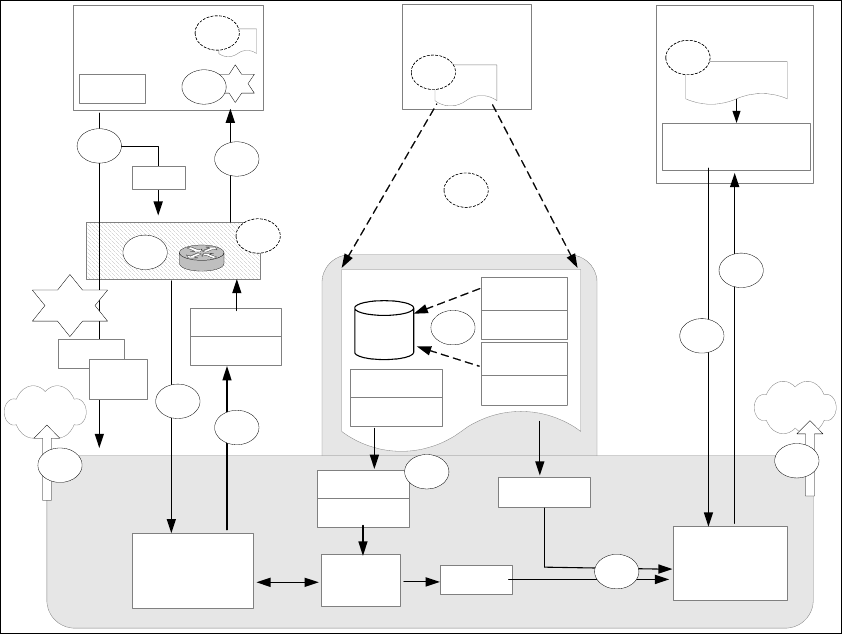
56 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
The flow consists of these process groups, depicted in Figure 3-6:
1. Policy creation and deployment
2. Posture collection
3. Posture validation and policy enforcement
4. Remediation
Figure 3-6 Solution data and communication flow
The naming convention in the diagram has four flows based on the process.
Policy creation and deployment (flow 1)
The first step in the data flow is the creation and deployment of a policy. If a Tivoli
Configuration Manager server is used for remediation, a corresponding
Network
Rem.
Attributes
Rem.URL
SCM
Server
AAA Policy
Server
(ACS)
Policy
Policy Collector
Policy.Version
Posture
Plug-in
Policy.Version
Violation.Count
Policy.Version
Violation.Count
TCM
Server
Cisco Trust
Agent
Remediation
Handler
Rem.Object
TCM Web Gateway
NAD
Rem.URL
1.a
Posture
Collector
Rem.
Attributes
Posture
Collector
Rem.
Attributes
Posture
cache
1.b
1.c
1.d
2.a
2.b
3.a
3.b
3.c
3.d
4.a
4.b
4.c
3.e
ACL
3.f
3.g
Rem.URL
Posture
Token
Pop-up
Message
Network
4.d
Network
Client
1.e


















