22 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
access, this is an acceptable solution. Users are authenticated and placed into a
default network based on their identity. It is not until the user attempted access
across a NAC-enabled router that the integrity check was performed.
With Layer 2 NAC, identity enforcement via 802.1x delivers access control by
checking authorization of the user to connect to the network. The identity can be
verified based on different means, such as user name/password or PKI public
certificates, but more importantly, it allows both identity and posture to be
validated before network access is granted. This allows users to be assigned into
specific networks based on their identity and assigned groups with
posture-based checking, providing an additional way to control a user’s traffic.
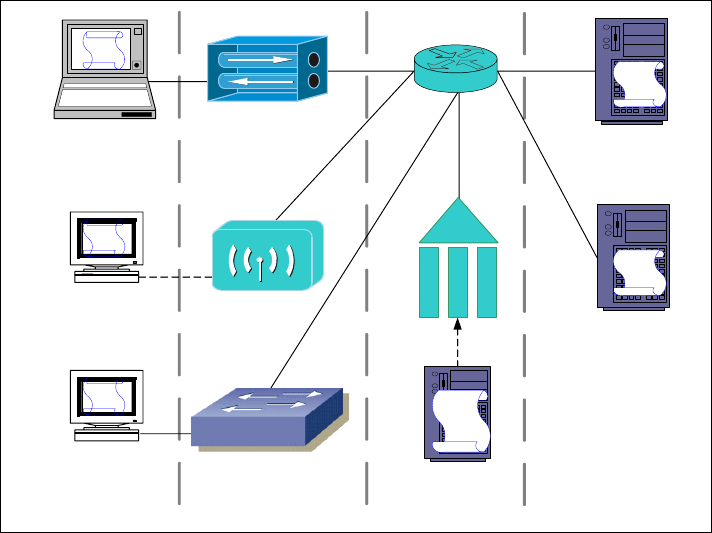
Figure 2-4 Layer 3 and Layer 2 NAC overview
Cisco NAC and IEEE 802.1x
An interesting terminology question to ask is: How does this solution relate to the
IEEE 802.1x protocol?
In this section we explain the basic difference and how
these two solutions can complement each other.
IEEE 802.1x is an identity-based network authentication protocol used at Layer 2
level to allow or disallow a specific user to connect to the network based on user
or machine credentials.
SCM policy enabled Layer 2 NAC Layer 3 NAC SCM policy enabled
Laptop computer
SCM
Policy
VPN
Concentrator
Intranet
Server
Intranet
Server
A A A
Cisco
Secure
ACS
Server
Wireless
Access Point
Desktop Client
SCM
Policy
PC Workstation
SCM
Policy
IBM SCM Server
SCM
Policy
Server
SCM
Policy
SCM
Policy
Workgroup Switch
NAC-
enabled
router


















