Appendix A. Hints and tips 451
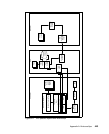
Communication port usage
Tivoli Security Compliance Manager server and client communicate only with
temporary connections. A persistent connection is not required because the
Security Compliance Manager/NAC concept can function without the Security
Compliance Manager server after the client policies are deployed.
Communications among Tivoli Security Compliance Manager components are
secured using 128-bit Secure Sockets Layer (SSL) encryption. The cipher suites
that are used are RSA_WITH_RC4_128_SHA, RSA_WITH_RC4_128_MD5,
and RSA_WITH_3DES_EDE_CBC_SHA.
Communication occurs using the Transmission Control Protocol (TCP) port
numbers specified during the installation of the server and the clients.
Communication between the clients and the server is performed using an
internal protocol.
Communications between the administration utilities and the server are handled
using the Java Remote Method Invocation (RMI) technology.
Summary of default port usage
Communications between the server and a push client:
– Server to client: TCP 1950
– Client to server: TCP 1951
Communications between the server and the administration console or
administration commands and administration utility:
– Server: TCP 1955 (RMI-naming) administration utility
Tools and tricks
This section includes some useful commands that can assist in troubleshooting
and problem determination.
Cisco NAC
The following Cisco router commands and other useful information about the
ACS server, which are unique to Network Admission Control, are provided below.
Note: These commands are listed mainly to assist in resolving problems in a
NAC setup; for any additional information about these or other commands, you
should refer to the Cisco product guides.