Decline Flo
w Control: Select the value to specify the Decline Flow Control. The traffic
flow of the corresponding port will be limited to be this value i
f
the transmission rate of the Decline packets exceeds the
Decline Threshold.
Option 82 Config
Option 82 Support: Enable/Disable the Option 82 feature.
Existed Option 82 field: Select the operation for the Option 82 field of the DHCP request
packets from the Host.
Keep: Indicates to keep the Option 82 field of the packets.
Replace: Indicates to replace the Option 82 field of the
packets with the switch defined one.
Drop: Indicates to discard the packets including the Option
82 field.
Circuit ID: Enter the sub-option Circuit ID for the customized Option 82.
Remote ID: Enter the sub-option Remote ID for the customized Option 82.
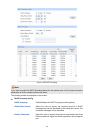
Port Config
Port Select: Click the Select button to quick-select the corresponding port
based on the port number you entered.
Select: Select your desired port for configuration. It is multi-optional.
Port: Displays the port number.
Trusted Port: Enable/Disable the port to be a Trusted Port. Only the Trusted
Port can receive the DHCP packets from DHCP servers.
MAC Verify: Enable/Disable the MAC Verify feature. There are two fields o
f
the DHCP packet containing the MAC address of the Host. The
MAC Verify feature is to compare the two fields and discard the
packet if the two fields are different.
Flow Control: Enable/Disable the Flow Control feature for the DHCP packets.
The excessive DHCP packets will be discarded.
Decline Protect: Enable/Disable the Decline Protect feature.
LAG: Displays the LAG to which the port belongs to.
12.2 ARP Inspection
According to the ARP Implementation Procedure stated in 12.1.3 ARP Scanning, it can be found
that ARP protocol can facilitate the Hosts in the same network segment to communicate with one
another or access to external network via Gateway. However, since ARP protocol is implemented
with the premise that all the Hosts and Gateways are trusted, there are high security risks during
ARP Implementation Procedure in the actual complex network. Thus, the cheating attacks against
ARP, such as imitating Gateway, cheating Gateway, cheating terminal Hosts and ARP Flooding
198