Port5 5 VLAN5
Port2 2 VLAN2
Port3 3 VLAN3
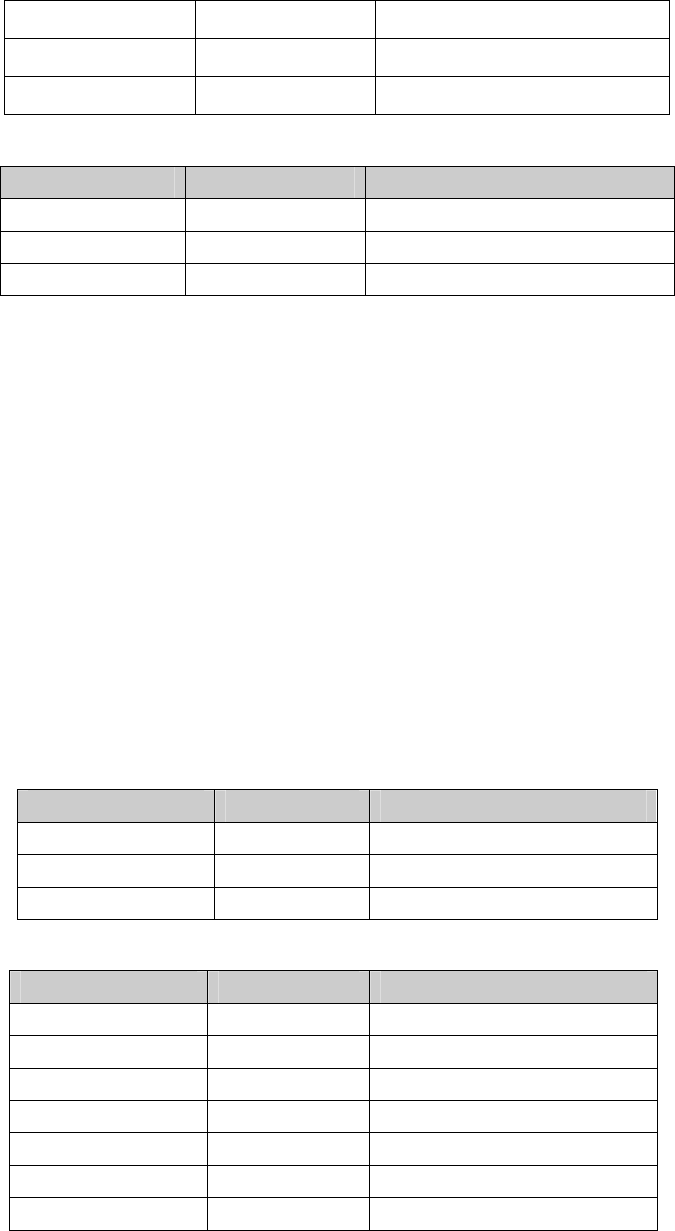
Table 6-4 Port settings before configuration synchronization
Port PVID Allowed VLANs
Port5 5 VLAN2, 3, 5
Port2 2 VLAN2, 5
Port3 3 VLAN2, 5
Table 6-5 Port settings after configuration synchronization
MAC address duplication: After port configuration synchronization, packets from Secondary
VLAN can be forwarded via the promiscuous port untagged, and those from Primary VLAN
can be sent via the host port untagged. In order for these packets can be forwarded in
unicast via the right port, MAC address duplication is used to expand the VLANs the MAC
address is in. Normally, the egress ports for forwarding these packets are identified through
MAC address learning. For example the switch in
Figure 6-15 maintains a MAC address
table shown in Table 6-6. The MAC address duplication process has
two aspects, that is,
duplicating the dynamic MAC addresses learned by the host ports in the secondary VLANs
to the Primary VLAN and copying the dynamic MAC addresses learned by the promiscuous
ports in the Primary VLAN to the secondary VLANs. As shown in
Figure 6-15, supposing the
Router sends a packet with the source MAC as mac_2 and the destination Mac as mac_a.
The MAC address table on the switch is changed to the one shown in Table 6-7.
Destination MAC VLAN Egress Port
mac_a 5 port 5
mac_2 2 port 2
mac_3 3 port 3
Table 6-6 MAC address table before duplication
Destination MAC VLAN Egress Port
mac_a 5 port 5
mac_a 2 port 5
mac_a 3 port 5
mac_2 2 port 2
mac_2 5 port 2
mac_3 3 port 3
mac_3 5 port 3
Table 6-7 MAC address table after duplication
Packet forwarding in Private VLAN
84


















