failing to p
ass community name authentication are discarded. The community name can limit
access to SNMP Agent from SNMP NMS, functioning as a password.
SNMP v2c: SNMP v2c also adopts community name authentication. It is compatible with SNMP
v1 while enlarges the function of SNMP v1.
SNMP v3: Basing on SNMP v1 and SNMP v2c, SNMP v3 extremely enhances the security and
manageability. It adopts VACM (View-based Access Control Model) and USM (User-Based
Security Model) authentication. The user can configure the authentication and the encryption
functions. The authentication function is to limit the access of the illegal user by authenticating the
senders of packets. Meanwhile, the encryption function is used to encrypt the packets transmitted
between SNMP Management Station and SNMP Agent so as to prevent any information being
stolen. The multiple combinations of authentication function and encryption function can
guarantee a more reliable communication between SNMP Management station and SNMP Agent.
MIB Introduction
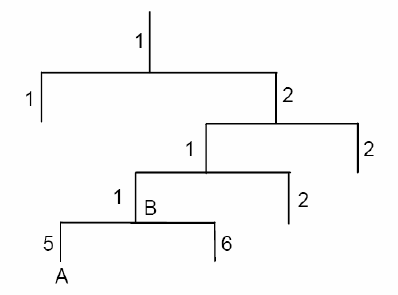
To uniquely identify the management objects of the device in SNMP messages, SNMP adopts the
hierarchical architecture to identify the managed objects. It is like a tree, and each tree node
represents a managed object, as shown in the following figure. Thus the object can be identified
with the unique path starting from the root and indicated by a string of numbers. The number string
is the Object Identifier of the managed object. In the following figure, the OID of the managed
object B is {1.2.1.1}. While the OID of the managed object A is {1.2.1.1.5}.
Figure 13-2 Architecture of the MIB tree
SNMP Configuration Outline
1. Create View
The SNMP View is created for the SNMP Management Station to manage MIB objects. The
managed object, uniquely identified by OID, can be set to under or out of the management of
SNMP Management Station by configuring its view type (included/excluded). The OID of managed
object can be found on the SNMP client program running on the SNMP Management Station.
2. Create SNMP Group
After creating the SNMP View, it’s required to create an SNMP Group. The Group Name, Security
Model and Security Level compose the identifier of the SNMP Group. The Groups with these three
items the same are considered to be the same. You can configure SNMP Group to control the
network access by providing the users in various groups with different management rights via the
Read View, Write View and Notify View.
3. Create SNMP User
The User configured in an SNMP Group can manage the switch via the client program on
management station. The specified User Name and the Auth/Privacy Password are used for
SNMP Management Station to access the SNMP Agent, functioning as the password.
221


















