39
Enhancements
Release K.12.05 Enhancements
Therefore, on a port where one or more authenticated client sessions are already running, all
such clients are on the same untagged VLAN. If a RADIUS server subsequently authenticates a
new client, but attempts to re-assign the port to a different, untagged VLAN than the one already
in use for the previously existing, authenticated client sessions, the connection for the new client
will fail. For more on this topic, refer to “802.1X Open VLAN Mode” in the “Configuring Port-Based
and Client-Based Access Control (802.1X)” chapter in the Access Security Guide.
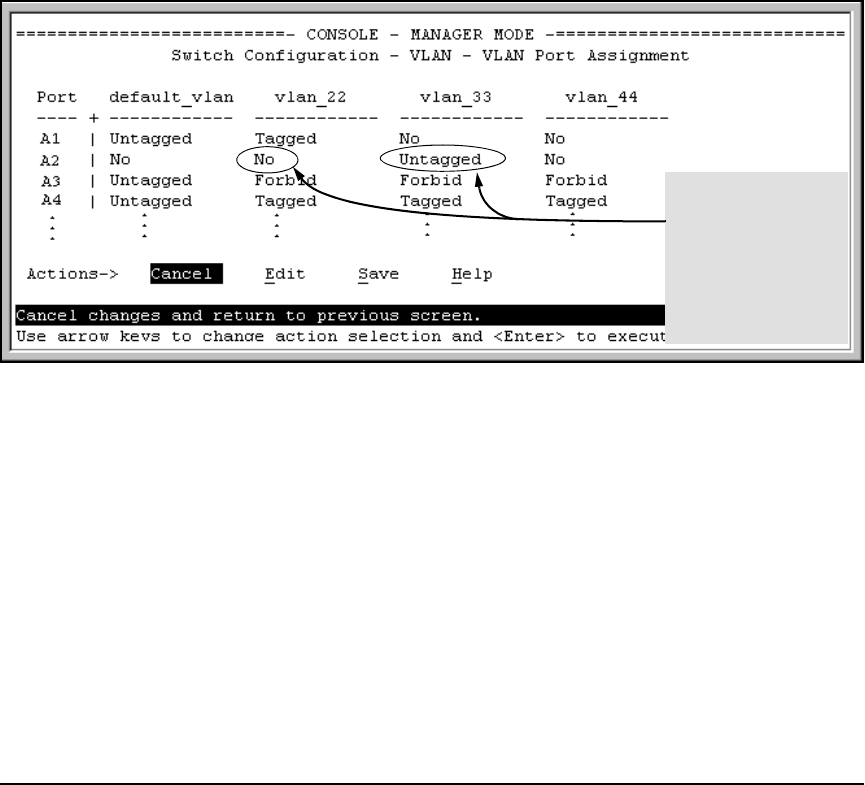
Example of Untagged VLAN Assignment in a RADIUS-Based Authentication Session
The following example shows how an untagged static VLAN is temporarily assigned to a port for use
during an 802.1X authentication session. In the example, an 802.1X-aware client on port A2 has been
authenticated by a RADIUS server for access to VLAN 22. However, port A2 is not configured as a
member of VLAN 22 but as a member of untagged VLAN 33 as shown in Figure 1.
Figure 1. Example of an Active VLAN Configuration in the Menu Interface View
In Figure 1, if RADIUS authorizes an 802.1X client on port A2 with the requirement that the client
use VLAN 22, then:
■ VLAN 22 becomes available as Untagged on port A2 for the duration of the session.
■ VLAN 33 becomes unavailable to port A2 for the duration of the session (because there can
be only one untagged VLAN on any port).
To view the temporary VLAN assignment as a change in the active configuration, use the show vlan
<vlan-id> command as shown in Figure 2, where <vlan-id> is the (static or dynamic) VLAN used in the
authenticated client session.
Scenario: An authorized
802.1X client requires
access to VLAN 22 from
port A2. However,
access to VLAN 22 is
blocked (not untagged
or tagged) on port A2
and VLAN 33 is untagged
on port A2.


















