Chapter 15 - Configuring IPsec VPN
IPsec VPN Connection Details
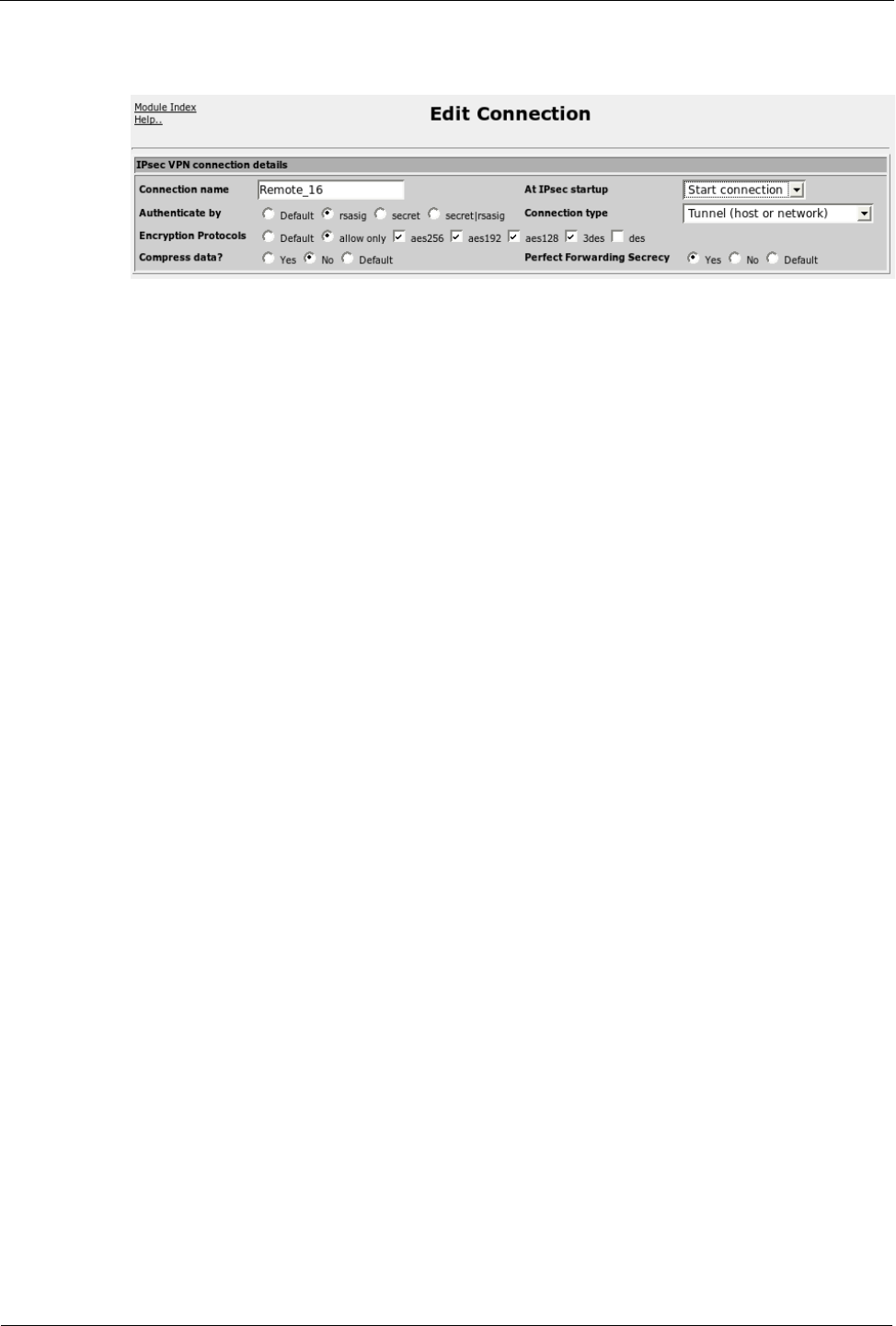
The Connection name field associates a name with the connection. Do not embed
whitespace in the name.
The At IPsec startup field determines what happens to the connection after
Openswan starts and includes the options “Ignore”, “Add connection”, “Start
Connection”, “Route” and “Default”. A value of “Ignore” will cause the connection
to be ignored. A value of “Add connection” will cause the connection to be
established when explicitly started (via command line or the IPsec VPN
Configuration menu “Start Connection” button). If “Start connection” is chosen then
the connection will be authorized when Openswan is started, but not activated until an
incoming request arrives. A value of “Route” will cause a route (and only the route)
for packets to be established, discarding packets sent there, which may be preferable
to having them sent elsewhere based on a more general route (e.g., a default route).
The Authenticate by fields select the authentication method. If “Default” is selected
the value in the “Defaults for all connections” record is used. If “rsasig” or “secret|
rsasig” is selected then the System's public key of each of the Left System's Settings
and Right System's Settings sections must include an RSA signature string or an
X.509 certificate must be in use. If “secret” is selected then the Preshared key menu
must contain a key indexed by the Public IPs of the Left and Right systems.
The Encryption Protocols fields select the encryption protocol used. If “Default” is
selected the value in the “Defaults for all connections” record is used. If “allow only”
is selected, the protocols in “aes256”, “aes192”, “aes128” and “3des”, are included in
a list. At connection time the two peers will compare their capabilities and select the
strongest common protocol (largest aes over smaller aes and aes over 3des).
The Compress data? fields will select whether data should be compressed. If
“Default” is selected the value in the “Defaults for all connections” record is used.
The Perfect Forward Secrecy fields will enable PFS, causing keys to be exchanged
in a manner which provides attackers that have compromised a key with no advantage
in decoding previously intercepted packets or with subsequent packets. Not all
clients support PFS.
RuggedCom 145
Figure 126: Editing A VPN Connection, Part 1


















