25-10
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 25 Configuring the ASA for Cisco Cloud Web Security
Configuring Cisco Cloud Web Security
(Multiple Context Mode) Allowing Cloud Web Security Per Security Context
In multiple context mode, you must allow Cloud Web Security per context. See the “Configuring a
Security Context” section on page 8-20 in the general operations configuration guide.
Note You must configure a route pointing to the Scansafe towers in both; the admin context and the specific
context. This ensures that the Scansafe tower does not become unreachable in the Active/Active failover
scenario.
Configuring a Service Policy to Send Traffic to Cloud Web Security
Your service policy consists of multiple service policy rules, applied globally, or applied to each
interface. Each service policy rule can either send traffic to Cloud Web Security (Match) or exempt
traffic from Cloud Web Security (Do Not Match). Create rules for traffic destined for the Internet. The
order of these rules is important. When the ASA decides whether to forward or exempt a packet, the ASA
tests the packet with each rule in the order in which the rules are listed. After a match is found, no more
rules are checked. For example, if you create a rule at the beginning of a policy that explicitly Matches
all traffic, no further statements are ever checked. You can reorder the rules as needed after you add them.
See Chapter 1, “Configuring a Service Policy,” for more information about service policy rules.
Prerequisites
(Optional) If you need to use a whitelist to exempt some traffic from being sent to Cloud Web Security,
first create the whitelist according to the “(Optional) Configuring Whitelisted Traffic” section on
page 25-23 so you can refer to the whitelist in your service policy rule.
Detailed Steps
Step 1 Choose Configuration > Firewall > Service Policy Rules, and click Add > Service Policy Rule to add
a service policy rule.
Step 2 On the Service Policy dialog box, you can configure Cloud Web Security as part of a new service policy,
or you can edit an existing service policy. Click Next.
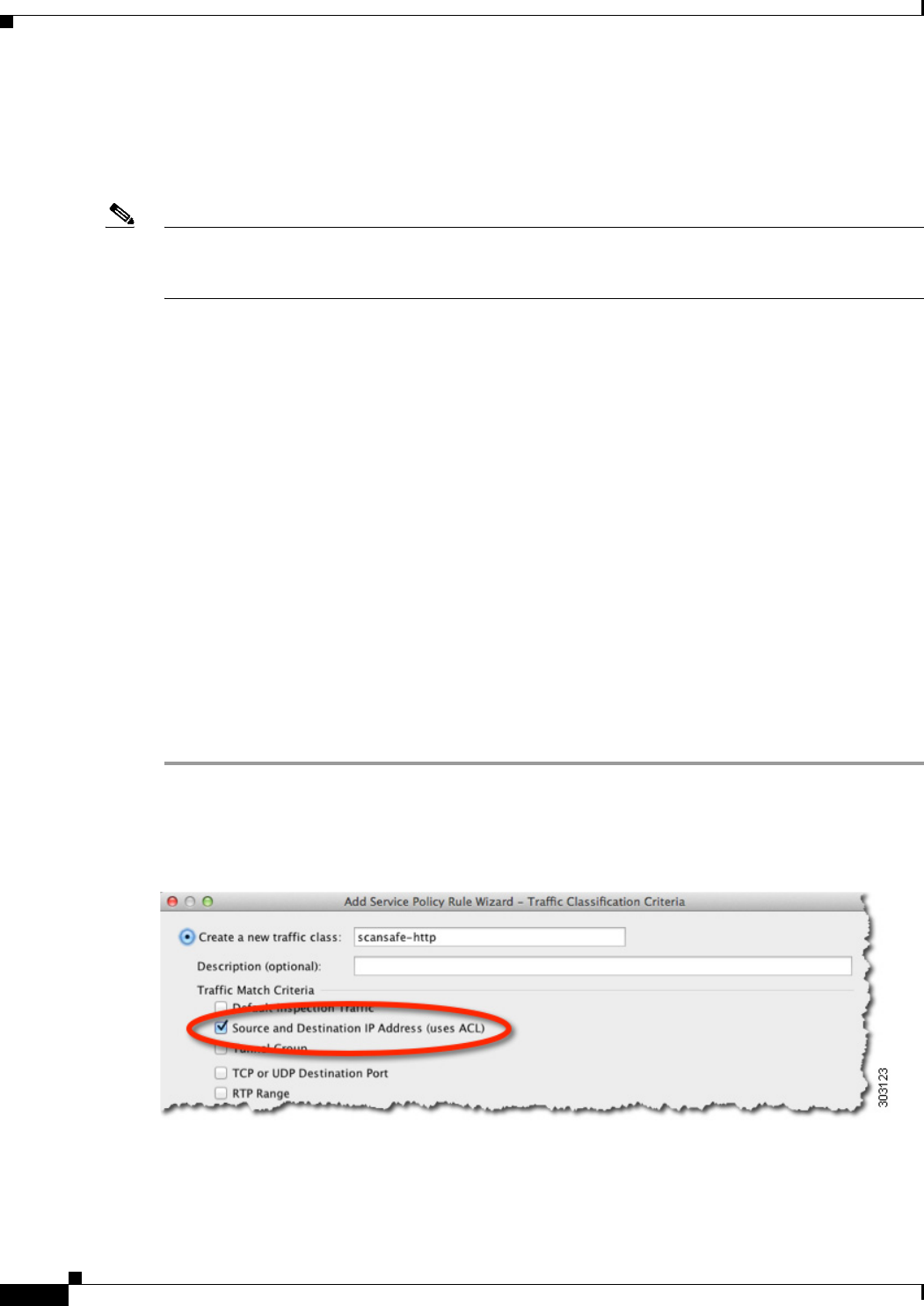
Step 3 On the Traffic Classification Criteria dialog box, name the traffic class (or accept the default name), keep
the Create a new traffic class option selected, and click Source and Destination IP address (Uses
ACL), then click Next.
