3-21
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 3 Information About NAT (ASA 8.3 and Later)
NAT Interfaces
For section 2 rules, for example, you have the following IP addresses defined within network objects:
192.168.1.0/24 (static)
192.168.1.0/24 (dynamic)
10.1.1.0/24 (static)
192.168.1.1/32 (static)
172.16.1.0/24 (dynamic) (object def)
172.16.1.0/24 (dynamic) (object abc)
The resultant ordering would be:
192.168.1.1/32 (static)
10.1.1.0/24 (static)
192.168.1.0/24 (static)
172.16.1.0/24 (dynamic) (object abc)
172.16.1.0/24 (dynamic) (object def)
192.168.1.0/24 (dynamic)
NAT Interfaces
You can configure a NAT rule to apply to any interface (in other words, all interfaces), or you can identify
specific real and mapped interfaces. You can also specify any interface for the real address, and a specific
interface for the mapped address, or vice versa.
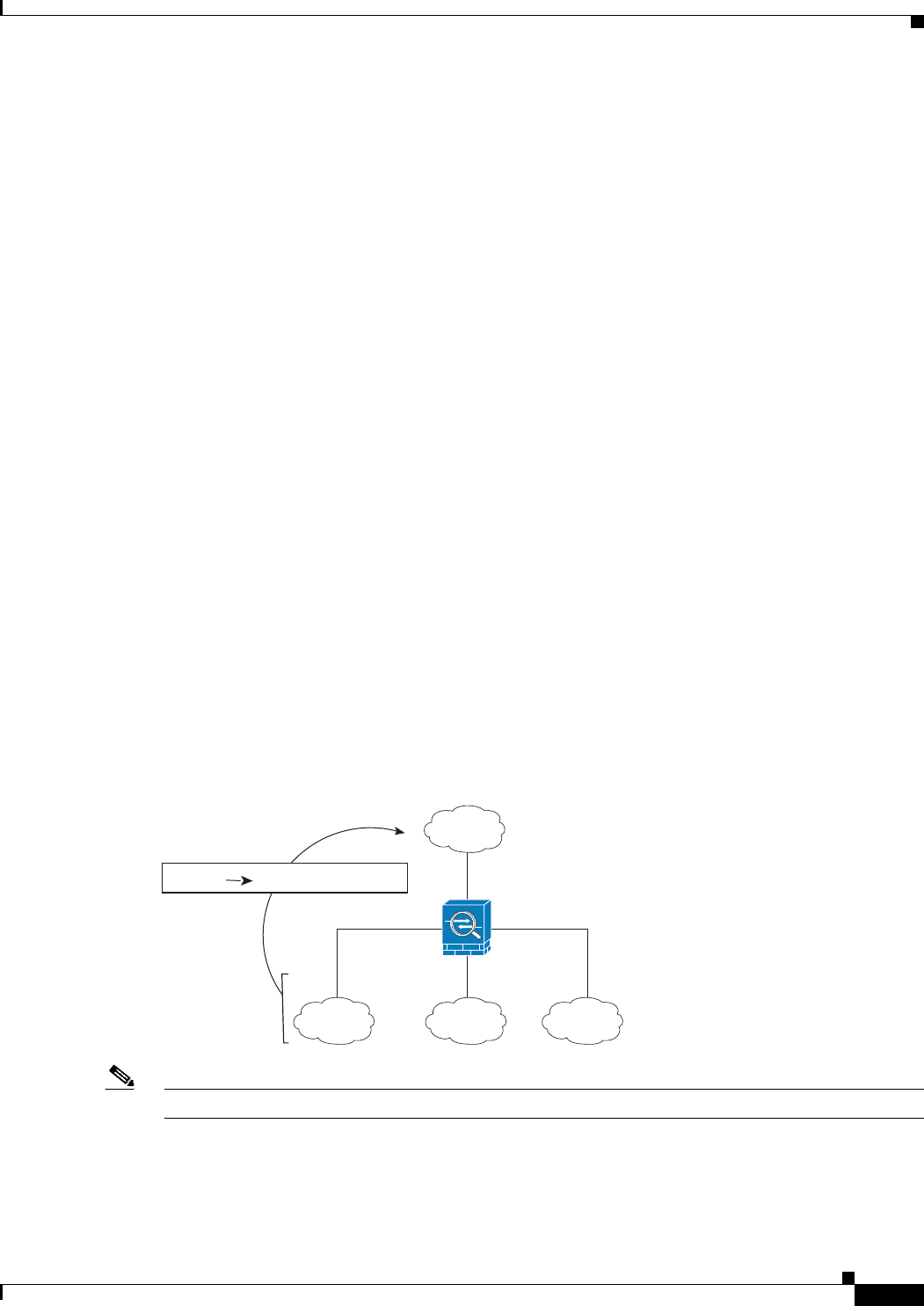
For example, you might want to specify any interface for the real address and specify the outside
interface for the mapped address if you use the same private addresses on multiple interfaces, and you
want to translate them all to the same global pool when accessing the outside (Figure 3-17).
Figure 3-17 Specifying Any Interface
Note For transparent mode, you must choose specific source and destination interfaces.
Outside
Mktg
10.1.2.0 10.1.2.010.1.2.0
Security
Appliance
Eng HR
10.1.2.0 209.165.201.1:xxxx
any
248768


















