11-16
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 11 Configuring Inspection of Basic Internet Protocols
DNS Inspection
map that have the same match, then the order in the configuration determines which match is used, so
these buttons are enabled. See the “Guidelines and Limitations” section on page 2-2 for more
information.
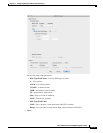
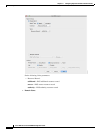
Step 10 Click OK to save the DNS inspect map.
Step 11 Click Apply.
Configuring DNS Inspection
The default ASA configuration includes many default inspections on default ports applied globally on
all interfaces. A common method for customizing the inspection configuration is to customize the
default global policy. The steps in this section show how to edit the default global policy, but you can
alternatively create a new service policy as desired, for example, an interface-specific policy.
Detailed Steps
Step 1 Configure a service policy on the Configuration > Firewall > Service Policy Rules pane according to
Chapter 1, “Configuring a Service Policy.”
You can configure DNS inspection as part of a new service policy rule, or you can edit an existing service
policy.
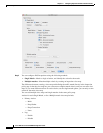
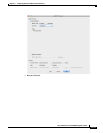
Step 2 On the Rule Actions dialog box, click the Protocol Inspections tab.
Step 3 (To change an in-use policy) If you are editing any in-use policy to use a different DNS inspection policy
map, you must disable the DNS inspection, and then re-enable it with the new DNS inspection policy
map name:
a. Uncheck the DNS check box.
b. Click OK.
c. Click Apply.
d. Repeat these steps to return to the Protocol Inspections tab.
Step 4 Check the DNS check box.
Step 5 Click Configure.
The Select DNS Inspect Map dialog appears.
Step 6 Choose the inspection map:
• To use the default map, click Use the default DNS inspection map (preset_dns_map).
• To use a DNS inspection policy map that you configured in the “(Optional) Configuring a DNS
Inspection Policy Map and Class Map” section on page 11-3, select the map name.
• To add a new map, click Add. See the “(Optional) Configuring a DNS Inspection Policy Map and
Class Map” section on page 11-3 for more information.
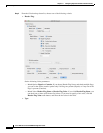
Step 7 If you use the Botnet Traffic Filter, click Enable Botnet traffic filter DNS snooping. Botnet Traffic
Filter snooping compares the domain name with those on the dynamic database or static database, and
adds the name and IP address to the Botnet Traffic Filter DNS reverse lookup cache. This cache is then
used by the Botnet Traffic Filter when connections are made to the suspicious address. We suggest that
you enable DNS snooping only on interfaces where external DNS requests are going. Enabling DNS
snooping on all UDP DNS traffic, including that going to an internal DNS server, creates unnecessary