3-25
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 3 Information About NAT (ASA 8.3 and Later)
NAT for VPN
Figure 3-20 Routed Mode Egress Interface Selection
NAT for VPN
• NAT and Remote Access VPN, page 3-25
• NAT and Site-to-Site VPN, page 3-27
• NAT and VPN Management Access, page 3-29
• Troubleshooting NAT and VPN, page 3-31
NAT and Remote Access VPN
Figure 3-21 shows both an inside server (10.1.1.6) and a VPN client (209.165.201.10) accessing the
Internet. Unless you configure split tunnelling for the VPN client (where only specified traffic goes
through the VPN tunnel), then Internet-bound VPN traffic must also go through the ASA. When the VPN
traffic enters the ASA, the ASA decrypts the packet; the resulting packet includes the VPN client local
address (10.3.3.10) as the source. For both inside and VPN client local networks, you need a public IP
address provided by NAT to access the Internet. The below example uses interface PAT rules. To allow
the VPN traffic to exit the same interface it entered, you also need to enable intra-interface
communication (AKA “hairpin” networking).
Real: 10.1.1.78
Mapped: 209.165.201.08
Inside
Untranslation
Packet
Eng
Dest. 209.165.201.08
10.1.1.78209.165.201.08
to
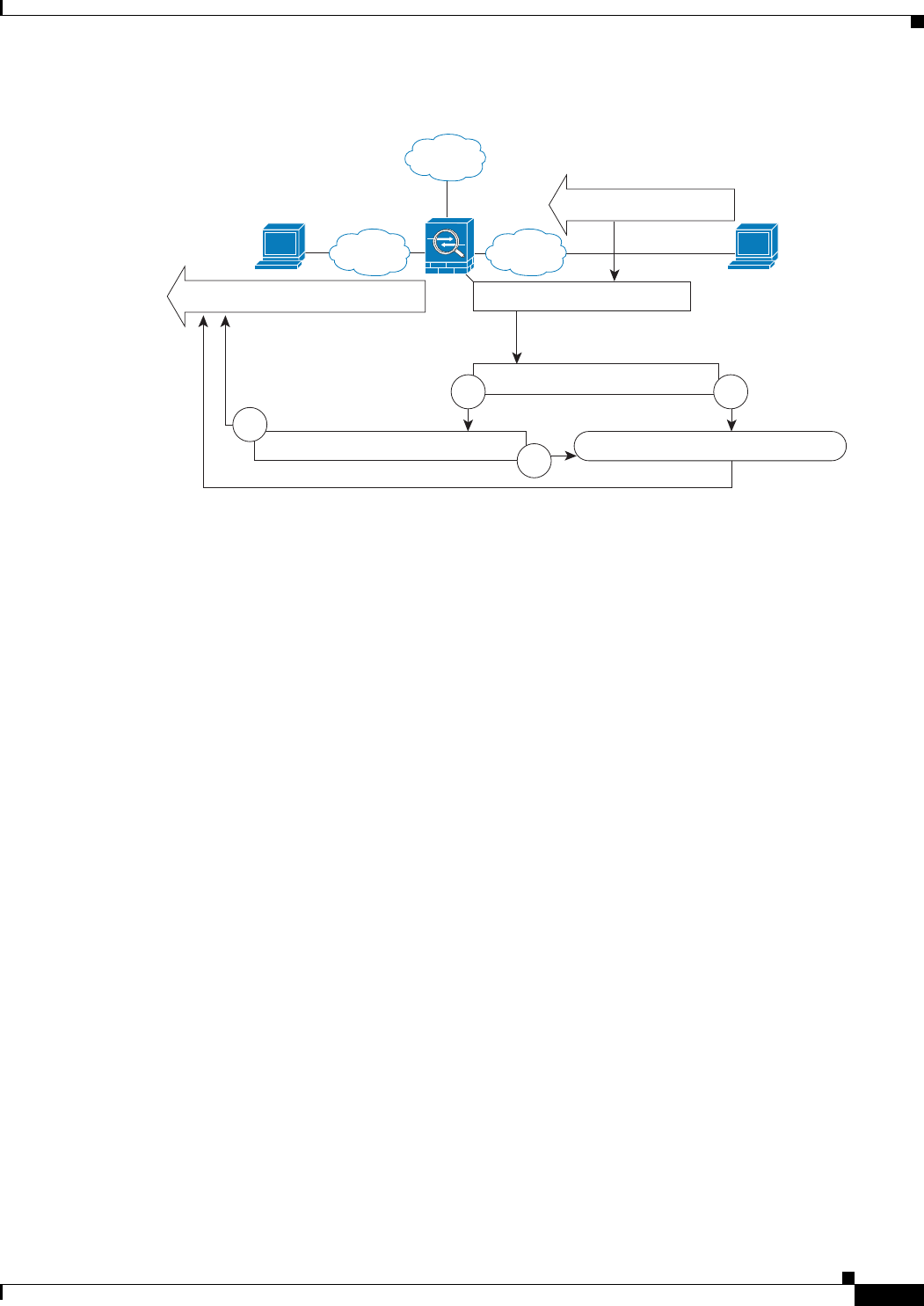
NAT rule specifies interface?
NAT rule specifies route lookup?
NoYe s
Ye s
No
Send packet out Inside interface.
Where to send 10.1.1.78?
Outside
Look up 10.1.1.78 in routing table.
370049


















