Configuring Switch Information 243
protection mechanism is invoked, and can provide various options. Unauthorized packets arriving
to a locked port are either forwarded, discarded with no trap, discarded with a trap or the ingress
port is disabled.
Locked port security also enables storing a list of MAC addresses in the configuration file. The
MAC address list can be restored after the device has been reset.
Disabled ports can only be activated from the
Port Configuration
page.
To open the
Port Security
page, select
Switch
→
Network Security
→
Port Security
.
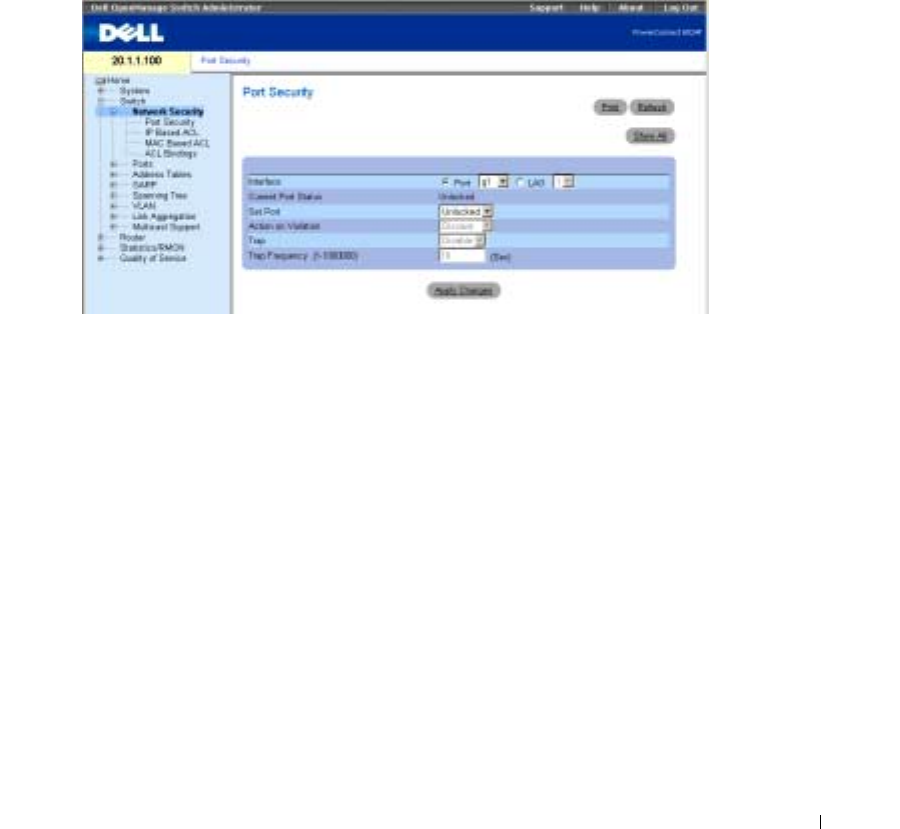
Figure 7-7. Port Security
Interface
— Indicates whether locked port security is enabled on a port or LAG.
Current Port Status
— Indicates if the port is currently locked and disabled, or if it is unlocked.
Set Port
— Enables locking the port. When a port is locked, all the current addresses that had been
dynamically learned by the switch on that port, are transformed to static MAC addresses. When
the port is unlocked, they are removed from the static list.
Action on Violation
— Action applied to packets arriving on the port. The field is grayed if the port
is unlocked. Possible values are:
Discard
— Discards the packets from any unlearned source. This is the default value.
Forward
— Forwards the packets from an unknown source. The MAC address is not learned.
Shutdown
— Discards the packet from any unlearned source and sends a trap. In addition,
the ingress port is disabled.
Trap
— Enables or disables sending a trap when a packet is received on a locked port.
Trap Frequency
— Amount of time (seconds) between traps.


















