ZyAIR B-500 Wireless Access Point User’s Guide
Wireless Security 6-3
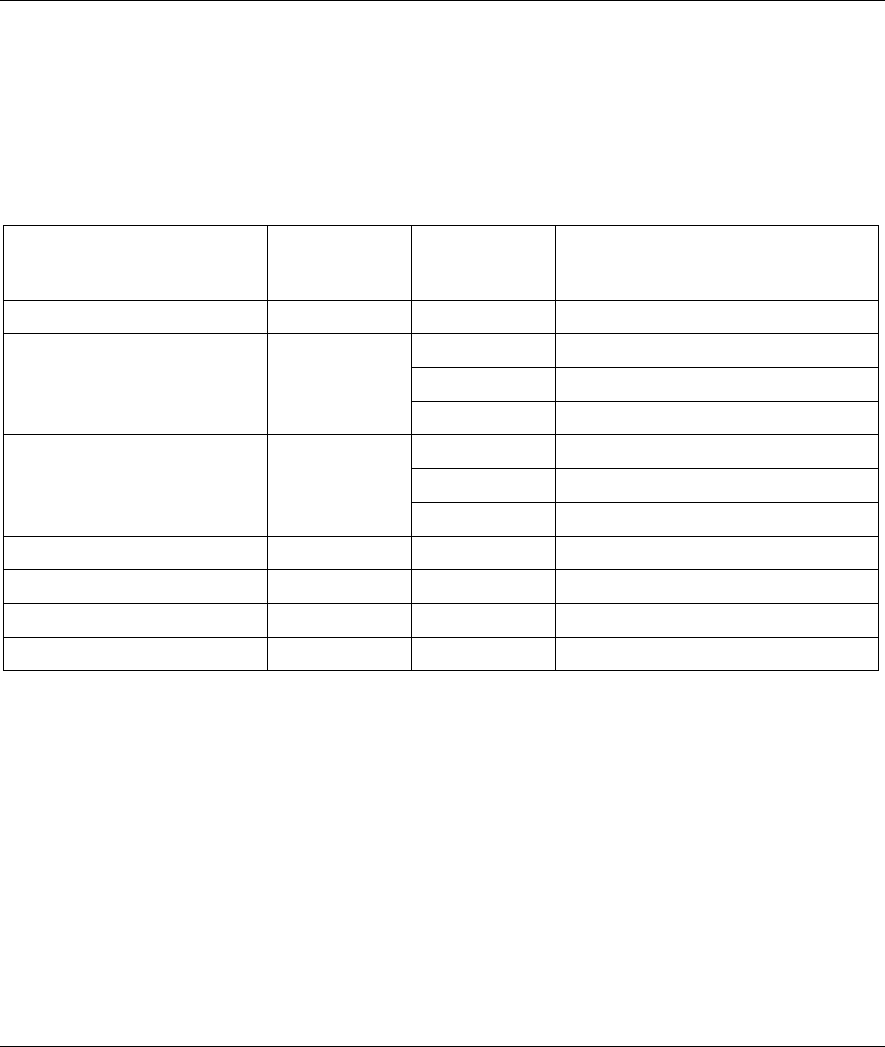
6.2 Security Parameters Summary
Refer to this table to see what other security parameters you should configure for each Authentication
Method/ key management protocol type. You enter manual keys by first selecting 64-bit WEP or 128-bit
WEP from the WEP Encryption field and then typing the keys (in ASCII or hexadecimal format) in the key
text boxes. MAC address filters are not dependent on how you configure these security features.
Table 6-2 Wireless Security Relational Matrix
AUTHENTICATION
METHOD/ KEY
MANAGEMENT PROTOCOL
ENCRYPTION
METHOD
ENTER
MANUAL KEY
IEEE 802.1X
Open None No Disable
No Enable with Dynamic WEP Key
Yes Enable without Dynamic WEP Key
Open WEP
Yes Disable
No Enable with Dynamic WEP Key
Yes Enable without Dynamic WEP Key
Shared WEP
Yes Disable
WPA WEP No Enable
WPA TKIP No Enable
WPA-PSK WEP Yes Enable
WPA-PSK TKIP Yes Enable
6.3 WEP Overview
WEP (Wired Equivalent Privacy) as specified in the IEEE 802.11 standard provides methods for both data
encryption and wireless station authentication.
6.3.1 Data Encryption
WEP provides a mechanism for encrypting data using encryption keys. Both the AP and the wireless stations
must use the same WEP key to encrypt and decrypt data. Your ZyAIR allows you to configure up to four 64-
bit or 128-bit WEP keys, but only one key can be enabled at any one time.


















