ZyAIR B-500 Wireless Access Point User’s Guide
6-4 Wireless Security
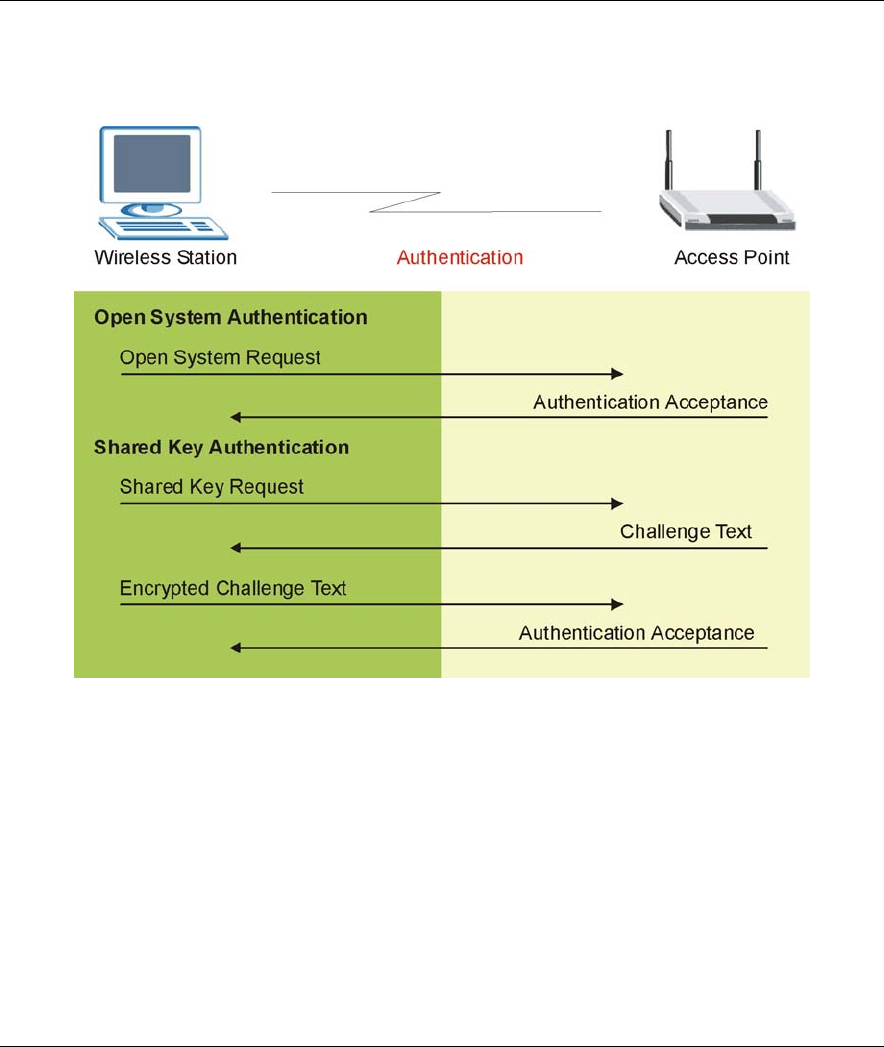
6.3.2 Authentication
Three different methods can be used to authenticate wireless stations to the network: Open System, Shared
Key, and Auto. The following figure illustrates the steps involved.
Figure 6-3 WEP Authentication Steps
Open system authentication involves an unencrypted two-message procedure. A wireless station sends an
open system authentication request to the AP, which will then automatically accept and connect the wireless
station to the network. In effect, open system is not authentication at all as any station can gain access to the
network.
Shared key authentication involves a four-message procedure. A wireless station sends a shared key
authentication request to the AP, which will then reply with a challenge text message. The wireless station
must then use the AP’s default WEP key to encrypt the challenge text and return it to the AP, which attempts
to decrypt the message using the AP’s default WEP key. If the decrypted message matches the challenge text,
the wireless station is authenticated. This requires you to enable the WEP encryption and specify a WEP key
on both the wireless station and the AP.


















