2. There are no output fields on EXEC CICS ENQ and DEQ requests.
Modifying the EID: It is not possible to modify the EID to make major changes to
requests. It is not possible, for example, to change an ENQ request to a DEQ
request. However, you can make minor changes to requests, such as to turn on the
existence bit for LENGTH. The list that follows shows the bits in the EID that can be
modified. Any attempt to modify any other part of the EID is ignored.
NQ_BITS1
X'40' The existence bit for LENGTH
X'20' The existence bit for MAXLIFETIME.
NQ_EIDOPT7
A user exit program at XNQEREQ can set the following on or off for ENQ
commands:
X'04' The existence bit for NOSUSPEND.
The EID is reset to its original value before return to the application program. That
is, changes made to the EID are retained for the duration of the enqueue request
only.
Note: Your user exit program is prevented from making major changes to the EID.
However, you must take great care when making the minor modifications
that are permitted.
Use of the task token UEPTSTOK: UEPTSTOK provides the address of a 4-byte
area that you can use to pass information between successive enqueue requests in
the same task. (By contrast, UEPNQTOK is usable only for the duration of a single
enqueue request, because its contents may be destroyed at the end of the
request.) For example, if you need to pass information between successive
invocations of the XNQEREQ exit, UEPTSTOK provides a means of doing this.
Note:
1. The lifetime of the area pointed to by UEPTSTOK is the lifetime of the
task.
2. The value of UEPTSTOK is shared by all the exits to which it is passed
during the lifetime of the task.
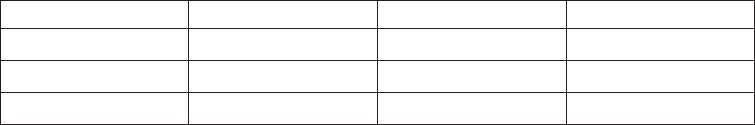
Table 3. User arguments and associated keywords, data types, and input/output types
Argument Keyword Data type Input/output type
Arg1 RESOURCE DATA-AREA input
Arg2 LENGTH BIN(15) input
Arg3 MAXLIFETIME CVDA input
Modifying user arguments: User exit programs can modify user input arguments
by:
1. Obtaining sufficient storage to hold the modified argument
2. Setting the storage to the required value
3. Setting the associated pointer in the parameter list to the address of the
newly-acquired area.
Note:
Chapter 1. Global user exit programs 65


















