ProSafe VPN Firewall 200 FVX538 Reference Manual
Firewall Protection and Content Filtering 4-31
v1.0, August 2006
6. Click Add. The Port Triggering Rule will be added to the Port Triggering Rules table.
To edit or modify a rule:
1. Click Edit in the Action column opposite the rule you wish to edit. The Edit Port Triggering
Rule screen will display.
2. Modify any of the fields for this rule.
3. Click Reset to cancel any changes and return to the previous settings.
4. Click Apply to save your modifications. Your changes will appear in the Port Triggering
Rules table.
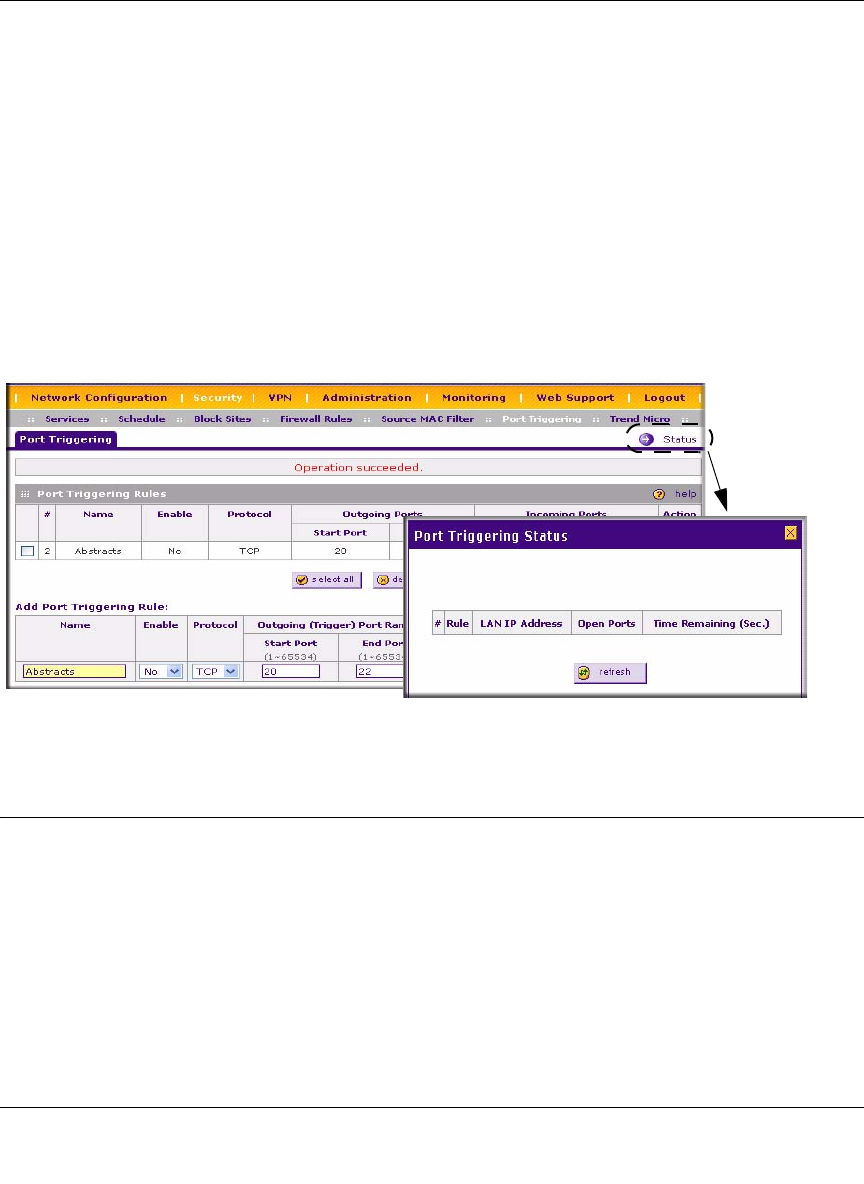
To check the status of the Port Triggering rules, click the Status link on the Port Triggering
screen.
E-Mail Notifications of Event Logs and Alerts
The Firewall Logs can be configured to log and then e-mail denial of access, general attack
information, and other information to a specified e-mail address. For example, your VPN firewall
will log security-related events such as: accepted and dropped packets on different segments of
your LAN or DMZ; denied incoming and outgoing service requests; hacker probes and Login
attempts; and other general information based on the settings you input on the Firewall Logs &
E-mail screen. In addition, if you have set up Content Filtering on the Block Sites screen (see
“Setting Block Sites (Content Filtering)” on page 4-25), a log will be generated when someone on
your network tries to access a blocked site.
Figure 4-20
