DHCP Snooping
3-233
3
If the DHCP snooping is globally disabled, all dynamic bindings are removed from
the binding table.
Additional considerations when the switch itself is a DHCP client – The port(s)
through which the switch submits a client request to the DHCP server must be
configured as trusted. Note that the switch will not add a dynamic entry for itself to
the binding table when it receives an ACK message from a DHCP server. Also,
when the switch sends out DHCP client packets for itself, no filtering takes place.
However, when the switch receives any messages from a DHCP server, any packets
received from untrusted ports are dropped.
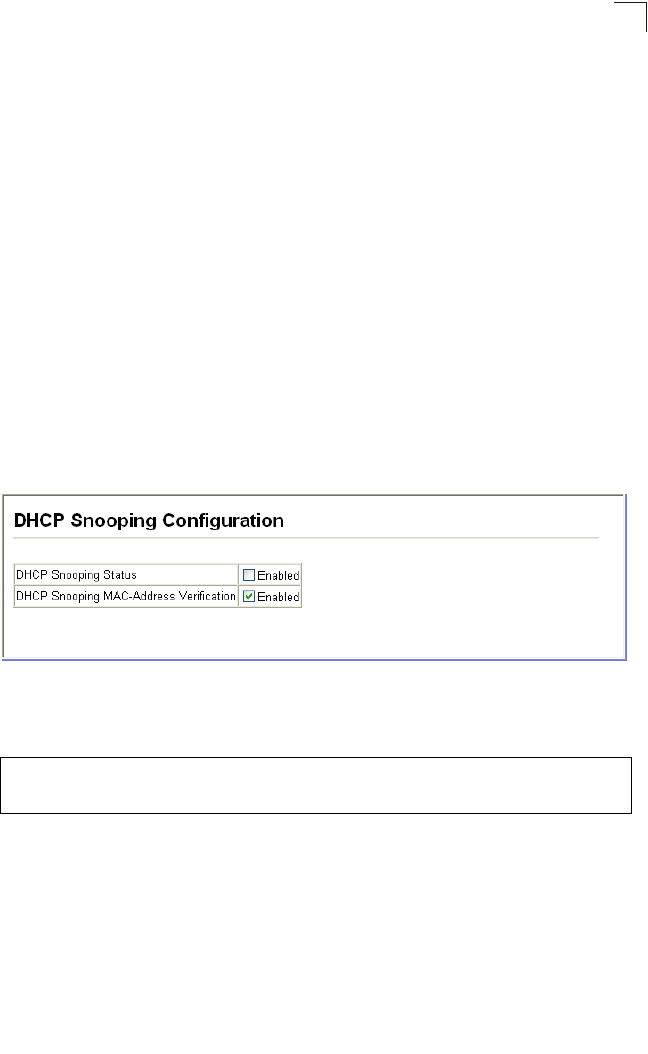
DHCP Snooping Configuration
Command Attributes
• DHCP Snooping Status – Enables or disables DHCP snooping globally.
• DHCP Snooping MAC-Address Verification – Enables or disables MAC address
verification. DHCP packets will be dropped if the source MAC address in the
Ethernet header of the packet is not same as the client’s hardware address in the
DHCP packet.
Web – Click DHCP Snooping, Configuration.
Figure 3-144 DHCP Snooping Configuration
CLI – This example first enables DHCP Snooping, and then enables DHCP
Snooping MAC-Address Verification.
DHCP Snooping VLAN Configuration
Enables DHCP snooping on the specified VLAN.
Command Attributes
• VLAN ID – ID of a configured VLAN. (Range: 1-4093)
• DHCP Snooping Status – Enables or disables DHCP snooping for the selected
VLAN. When DHCP snooping is enabled globally on the switch, and enabled on
the specified VLAN, DHCP packet filtering will be performed on any untrusted ports
within the VLAN.
Console(config)#ip dhcp snooping 4-317
Console(config)#ip dhcp snooping verify mac-address 4-321
Console(config)#


















