RX3141 User’s Manual Chapter 2 Getting to Know
5
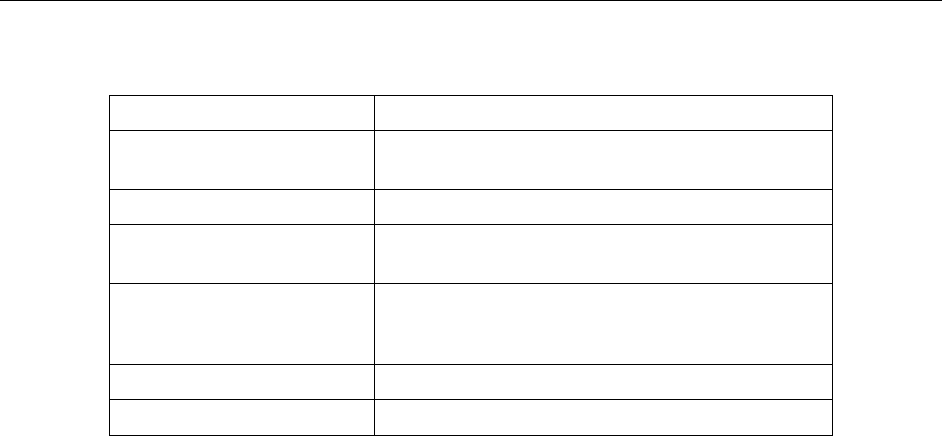
Table 2.1. DoS Attacks
Type of Attack Name of Attacks
Re-assembly attacks
Bonk, Boink, Teardrop (New Tear), Overdrop,
Opentear, Syndrop, Jolt, IP fragmentation overlap
ICMP Attacks Ping of Death, Smurf, Twinge
Flooders
Logging only for ICMP Flooder, UDP Flooder, SYN
Flooder
Port Scans
Logging only for TCP SYN Scan
Attack packets dropped: TCP XMAS Scan, TCP Null
Scan, TCP Stealth Scan
Protection with PF Rules Echo-Chargen, Ascend Kill
Miscellaneous Attacks IP Spoofing, LAND, Targa, Winnuke
2.4.1.1 Application Level Gateway (ALG)
Applications such as FTP open connections dynamically based on the respective application parameter. To go
through the firewall on the RX3141, packets pertaining to an application, require a corresponding allow rule. In
the absence of such rules, the packets will be dropped by the RX3141 Firewall. As it is not feasible to create
policies for numerous applications dynamically (at the same time without compromising security), intelligence
in the form of Application Level Gateways (ALG), is built to parse packets for applications and open dynamic
associations. The RX3141 NAT provides a number of ALGs for popular applications such as FTP, and
Netmeeting.
2.4.1.2 Log
Events in the network, that could be attempts to affect its security, are recorded in the RX3141 system log file.
The log maintains a minimum log details such as, time of packet arrival, description of action taken by Firewall
and reason for action.


















