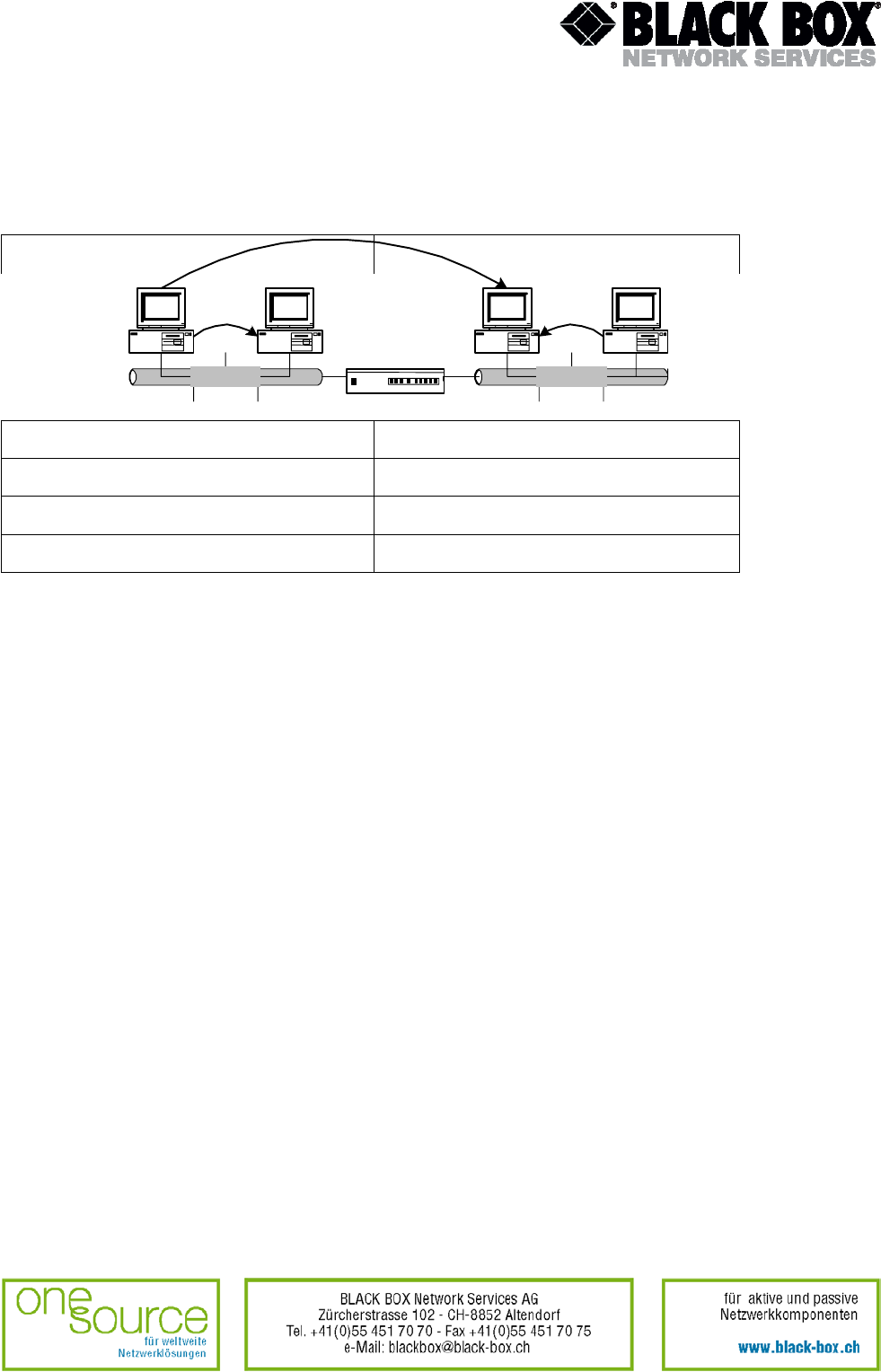
address table of a simple network consisting of two segments.
Fig.2 Simple network
Segment 2Segment 1
1
Bridge
2 3 4
Port 1
Port 2
MAC address Port
1 1
2 1
3 2
4 2
Each port work as an end node of the network segment. Originally, the bridge does not know
what nodes with what MAC addresses are connected to each of its port. That is why it sends any
received frame to all ports excluding the port from which the frame was received. Simultaneously
the bridge studies the source address of the frame and fills its table: what port (of a MAC
address) belongs to this or that segment.
Later, the bridge uses its table to forward the traffic. When one of the bridge interfaces receives
the information unit, the bridge seeks for the destination address in its internal table. If the table
contains an association between the destination address and any of the ports of this bridge,
excluding the one the information unit was received on, then the unit is forwarded from the
indicated port. If such an association is not established, the information is flooded to all ports,
except the inbound port. Broadcast and multicast-address messages are also flooded as in the
previous case.
Transparent bridges isolate in-segment traffic, thus reducing the traffic clearly seen in each
individual segment. This improves the response time of the network, seen by the user. The extent
of the traffic shortening and response-time improvement depends on the volume of intersegment
traffic relative to total traffic as well as the volume of the broadcast and multicast traffic.
One of the drawbacks that interfere with the “transparent bridge” algorithm is the presence of
network “loops”. It is shown in Fig.3:
Version: 1.0 Page. 22 of 95


















