Configuring the SSL VPN Client
SSL VPN User’s Guide 4-9
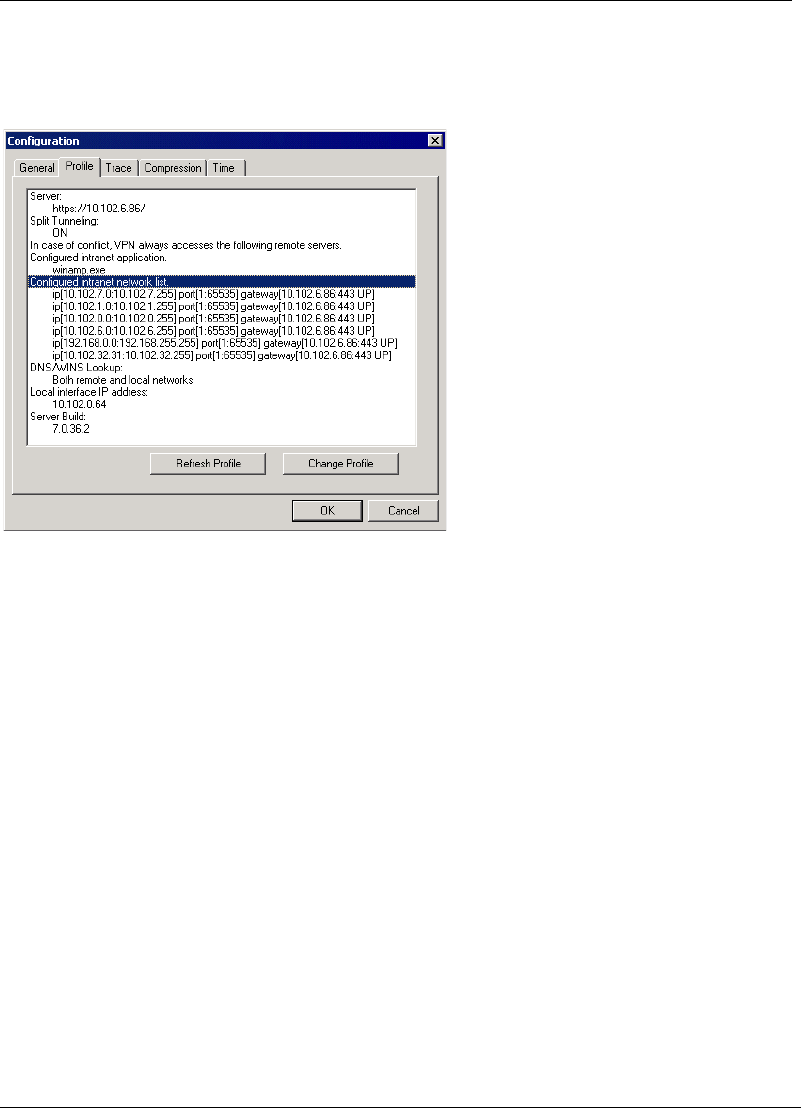
the traffic is sent to the local LAN or the Internet. You can view the list of IP
addresses, ports, and applications in the Profile pane of the Configuration dia-
log box as shown in the following figure.
Figure 4-8 List of IP addresses, ports, and applications
Consider a scenario where you have logged on to the SSL VPN and you need to
download a file from a computer on the local LAN. With split tunneling enabled,
you can directly connect to the computer via Windows Explorer and download
the file. This is because, the client intercepts your download request and learns
the destination IP address. As the IP address belongs to a computer in the
local LAN, the client does not send the request to the remote network via the
SSL VPN tunnel. Instead, it sends it directly to the local computer.
When Split Tunneling is disabled, all traffic is sent through the secure SSL VPN
tunnel thus bypassing the local LAN and the Internet. In fact, all DNS lookups
are sent to the DNS server on the remote network. As a result, you will not be
able to access resources on your local LAN.
For you to use this feature, the SSL VPN administrator first needs to configure
and enable it on the gateway. As part of the configuration process, the SSL
VPN administrator needs to specify ranges of IP addresses, ports, and applica-
tion names on the gateway. When the client intercepts traffic on your com-
puter, it compares the destination IP address, port, and application name in
the packets against the values configured by the SSL VPN administrator on the
gateway. If the values lie within one of the ranges, the client sends the packet
to the remote network. Else, it diverts it to the local LAN that your computer is
a part of.
This feature has three options:


















