200 User Guide Integrated Lights-Out
Using DNS-based restrictions can create some security complications. Name
service protocols are insecure. Any individual with malicious intent and access to
the network can place a rogue DNS service on the network creating fake address
restriction criteria. Organizational security policies should be taken into
consideration when implementing DNS-based address restrictions.
Role Address Restrictions
Role address restrictions are enforced by the LOM firmware, based on the client's
IP network address. When the address restrictions are met for a role, the rights
granted by the role apply.
Address restrictions can be difficult to manage if access is attempted across
firewalls or through network proxies. Either of these mechanisms can change the
apparent network address of the client, causing the address restrictions to be
enforced in an unexpected manner.
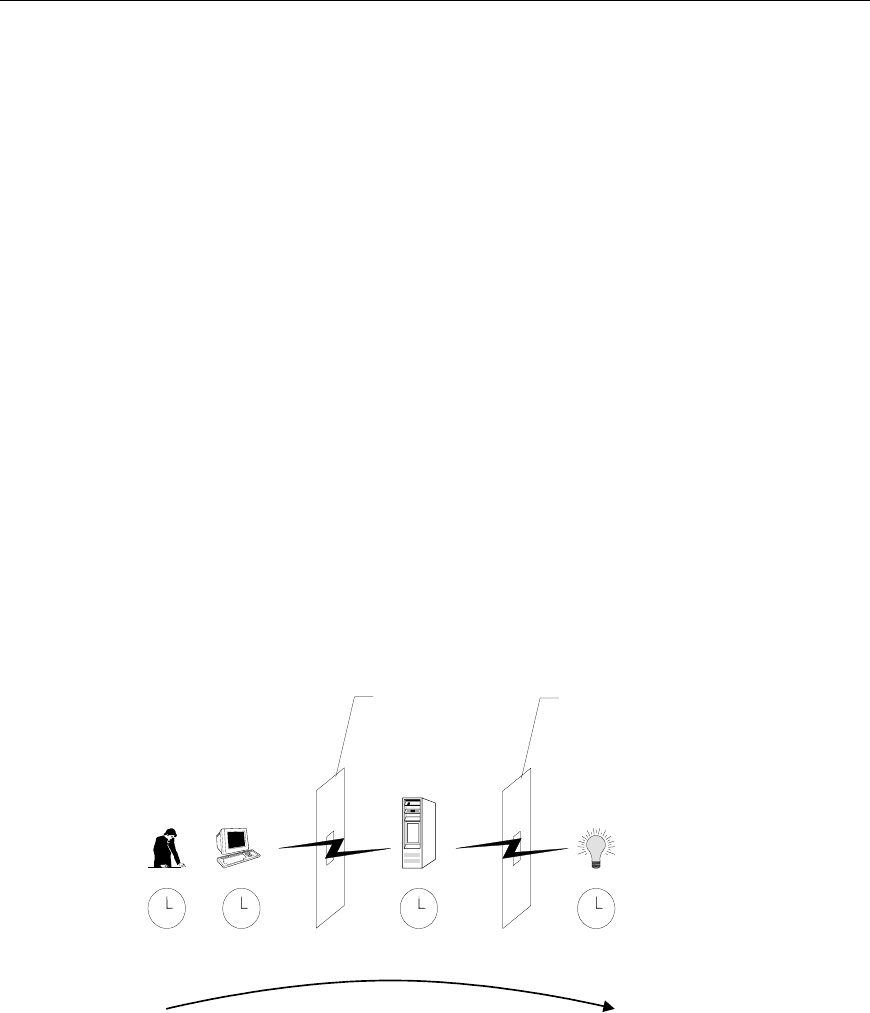
How Directory Login Restrictions are Enforced
Two sets of restrictions potentially limit a directory user's access to LOM
devices. User access restrictions limit a user's access to authenticate to the
directory. Role access restrictions limit an authenticated user's ability to receive
LOM privileges based on rights specified in one or more Roles.
75
6
12
11
10
84
2
1
93
75
6
12
11
10
84
2
1
93
75
6
12
11
10
84
2
1
93
User
Client
Workstation
Directory
Server
LOM
75
6
12
11
10
84
2
1
93
User restrictions must be met to
authenticate to the directory.
Enforced by the directory
server.
Role restrictions must be
met to receive rights
granted by 1 or more roles.
Enforced by LOM.
User access
restrictions
Role access
restrictions
And


















