Chapter 24 Firewall
ZyWALL USG 1000 User’s Guide
424
24.1.2 What You Need to Know
Stateful Inspection
The ZyWALL has a stateful inspection firewall. The ZyWALL restricts access by
screening data packets against defined access rules. It also inspects sessions. For
example, traffic from one zone is not allowed unless it is initiated by a computer in
another zone first.
Zones
A zone is a group of interfaces or VPN tunnels. Group the ZyWALL’s interfaces into
different zones based on your needs. You can configure firewall rules for data
passing between zones or even between interfaces and/or VPN tunnels in a zone.
Default Firewall Behavior
Firewall rules are grouped based on the direction of travel of packets to which they
apply. Here is the default firewall behavior for traffic going through the ZyWALL in
various directions.
To-ZyWALL Rules
Rules with ZyWALL as the To Zone apply to traffic going to the ZyWALL itself. By
default:
• The firewall allows only LAN, WAN computers to access or manage the ZyWALL.
• The ZyWALL drops most packets from the WAN zone to the ZyWALL itself,
except for VRRP traffic for Device HA and ESP/AH/IKE/NATT/HTTPS services for
VPN tunnels, and generates a log.
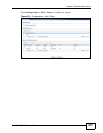
Table 108 Default Firewall Behavior
FROM ZONE TO ZONE BEHAVIOR
From WAN to ZyWALL Traffic from the WAN to the ZyWALL itself is allowed for certain
default services described in To-ZyWALL Rules on page 424. All
other WAN to ZyWALL traffic is dropped.
From WAN to any (other
than the ZyWALL)
Traffic from the WAN to any of the networks behind the
ZyWALL is dropped.
From DMZ to ZyWALL Traffic from the DMZ to the ZyWALL itself is allowed for certain
default services described in To-ZyWALL Rules on page 424. All
other DMZ to ZyWALL traffic is dropped.
From DMZ to any (other
than the ZyWALL)
Traffic from the DMZ to any of the networks behind the
ZyWALL is dropped.
From ANY to ANY Traffic that does not match any firewall rule is allowed. So for
example, LAN to WAN, LAN to DMZ, and LAN to WLAN traffic is
allowed. This also includes traffic to or from interfaces or VPN
tunnels that are not assigned to a zone (extra-zone traffic).