Chapter 46 Reports
ZyWALL USG 100/200 Series User’s Guide
734
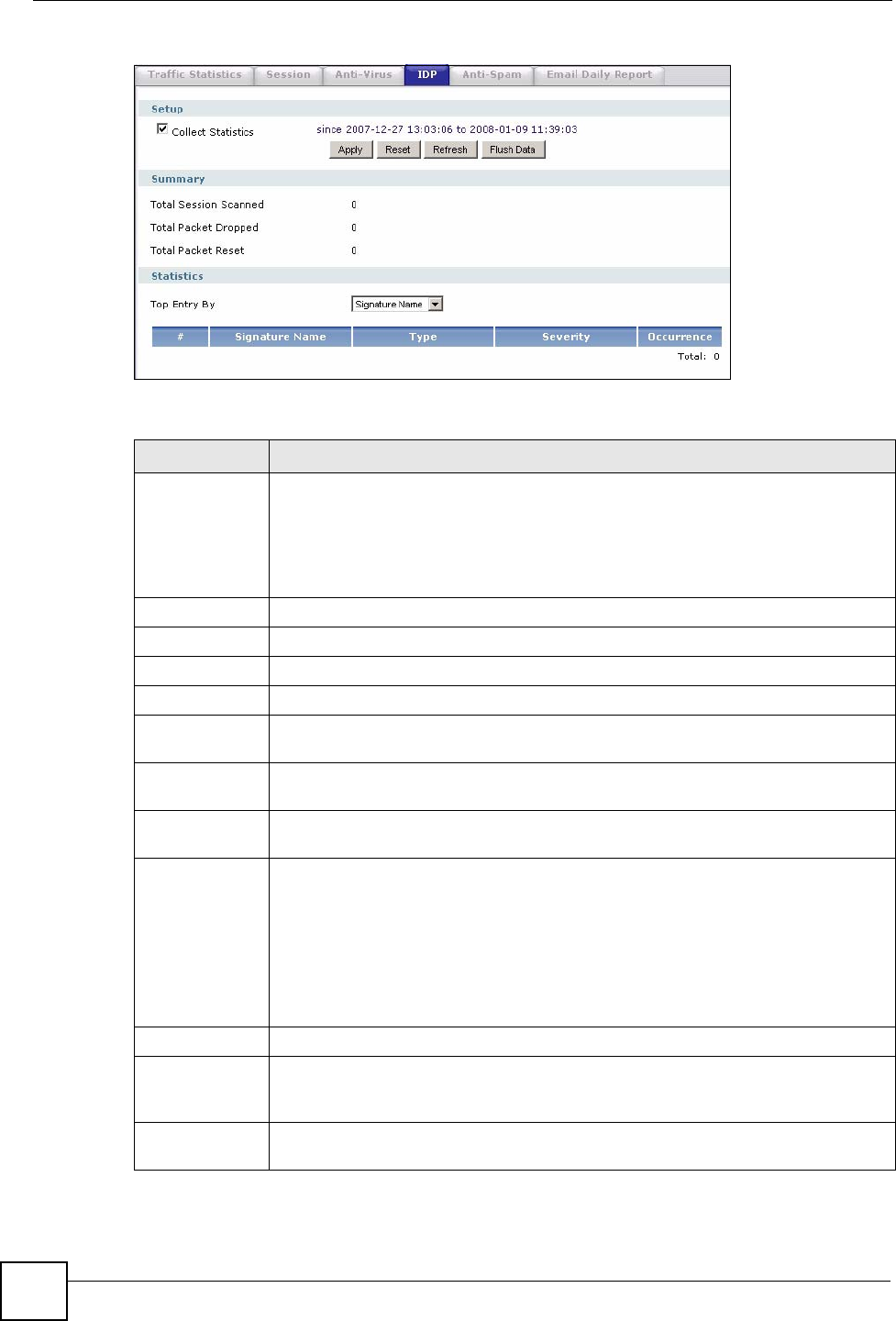
Figure 548 Maintenance > Report > IDP: Signature Name
The following table describes the labels in this screen.
Table 262 Maintenance > Report > IDP
LABEL DESCRIPTION
Collect
Statistics
Select this check box to have the ZyWALL collect IDP statistics.
The collection starting time displays after you click Apply. All of the statistics in this
screen are for the time period starting at the time displayed here. The format is year,
month, day and hour, minute, second. All of the statistics are erased if you restart
the ZyWALL or click Flush Data. Collecting starts over and a new collection start
time displays.
Apply Click Apply to save your changes back to the ZyWALL.
Reset Click Reset to begin configuring this screen afresh.
Refresh Click this button to update the report display.
Flush Data Click this button to discard all of the screen’s statistics and update the report display.
Total Sessions
Scanned
This field displays the number of sessions that the ZyWALL has checked for
intrusion characteristics.
Total Packet
Dropped
The ZyWALL can detect and drop malicious packets from network traffic. This field
displays the number of packets that the ZyWALL has dropped.
Total Packet
Reset
The ZyWALL can detect and drop malicious packets from network traffic. This field
displays the number of packets that the ZyWALL has reset.
Top Entry By Use this field to have the following (read-only) table display the top IDP entries by
Signature Name, Source or Destination.
Select Signature Name to list the most common signatures that the ZyWALL has
detected.
Select Source to list the source IP addresses from which the ZyWALL has detected
the most intrusion attempts.
Select Destination to list the most common destination IP addresses for intrusion
attempts that the ZyWALL has detected.
# This field displays the entry’s rank in the list of the top entries.
Signature Name This column displays when you display the entries by Signature Name. The
signature name identifies a specific intrusion pattern. Click the hyperlink for more
detailed information on the intrusion.
Type This column displays when you display the entries by Signature Name. It shows the
categories of intrusions. See Table 157 on page 493 for more information.


















