31
Enhancements in Release F.05.05 through F.05.70
Enhancements in Release F.05.05 through F.05.60
Authenticating One Switch to Another. 802.1X authentication also enables the switch to operate
as a supplicant when connected to a port on another switch running 802.1X authentication.
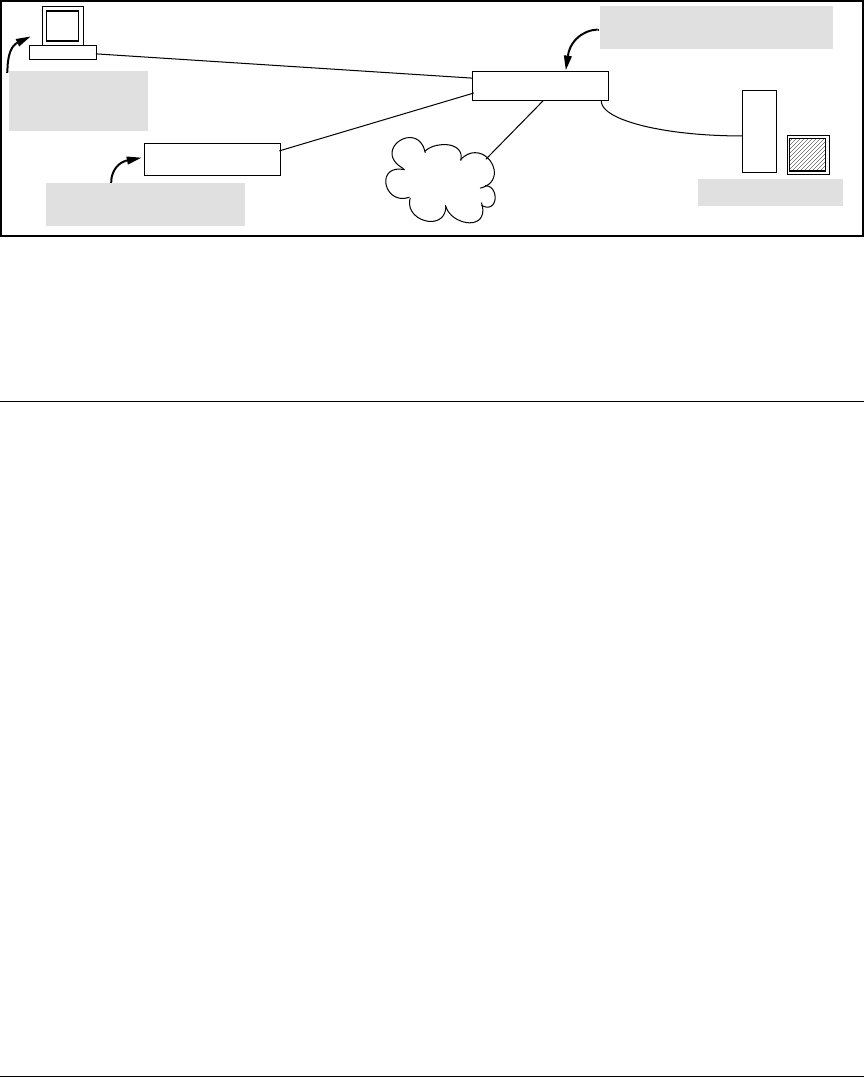
Figure 10. Example of an 802.1X Application
Accounting . The Series 2500 switches also provide RADIUS Network accounting for 802.1X access.
Refer to “Configuring RADIUS Authentication and Accounting” on page -102.
How 802.1X Operates
Authenticator Operation
This operation provides security on a direct, point-to-point link between a single client and the switch,
where both devices are 802.1X-aware. (If you expect desirable clients that do not have the necessary
802.1X supplicant software, you can provide a path for downloading such software by using the
802.1X Open VLAN mode—refer to “802.1X Open VLAN Mode” on page 44.) For example, suppose
that you have configured a port on the switch for 802.1X authentication operation. If you then connect
an 802.1X-aware client (supplicant) to the port and attempt to log on:
1. When the switch detects the client on the port, it blocks access to the LAN from that port.
2. The switch responds with an identity request.
3. The client responds with a user name that uniquely defines this request for the client.
4. The switch responds in one of the following ways:
• If 802.1X (port-access) on the switch is configured for RADIUS authentication, the
switch then forwards the request to a RADIUS server.
i. The server responds with an access challenge which the switch forwards to the client.
ii. The client then provides identifying credentials (such as a user certificate), which the
switch forwards to the RADIUS server.
iii. The RADIUS server then checks the credentials provided by the client.
RADIUS Server
LAN Core
802.1X-Aware Client
(Supplicant)
Switch Running 802.1X and
Connected as a Supplicant
Switch Running 802.1X and
Operating as an Authenticator


















