21.5 Example of Kerio VPN configuration: company with a filial office
315
For detailed description of basic configuration of WinRoute and of the local network,
refer to the Kerio WinRoute Firewall — Step By Step document.
3. In configuration of DNS Forwarder, set DNS forwarding rules for the domain in the
remote network. This enables to access hosts in the remote network by using their
DNS names (otherwise, it is necessary to specify remote hosts by IP addresses).
To provide correct forwarding of DNS requests from a WinRoute host, it is necessary
to use an IP address of a network device belonging to the host as the primary DNS
server. In DNS Forwarder configuration, at least one DNS server must be specified
to which DNS queries for other domains (typically the DNS server of the ISP).
Note: For proper functionality of DNS, the DNS database must include records for
hosts in a corresponding local network. To achieve this, save DNS names and IP
addresses of local hosts into the hosts file (if they use IP addresses) or enable co-
operation of the DNS Forwarder with the DHCP server (in case that IP addresses are
assigned dynamically to these hosts). For details, see chapter 5.3.
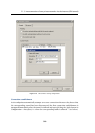
4. In the Interfaces section, allow the VPN server and set its SSL certificate if necessary.
Note the fingerprint of the server’s certificate for later use (it will be required for
configuration of the remote endpoint of the VPN tunnel).
Check whether the automatically selected VPN subnet does not collide with any local
subnet either in the headquarters or in the filial and select another free subnet if
necessary.
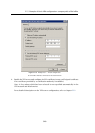
5. Define the VPN tunnel to the remote network. The passive endpoint of the tunnel
must be created at a server with fixed public IP address (i.e. at the headquarter’s
server). Only active endpoints of VPN tunnels can be created at servers with dynamic
IP address.
If the remote endpoint of the tunnel has already been defined, check whether the
tunnel was created. If not, refer to the Error log, check fingerprints of the certificates
and also availability of the remote server.
6. In traffic rules, allow traffic between the local network, remote network and VPN
clients and set desirable access restrictions. In this network configuration, all de-
sirable restrictions can be set at the headquarter’s server. Therefore, only traffic
between the local network and the VPN tunnel will be enabled at the filial’s server.
7. Test reachability of remote hosts from each local network. To perform the test, use
the ping and tracert system commands. Test availability of remote hosts both
through IP addresses and DNS names.