Chapter 3 Wizard Setup
ZyWALL 2WG User’s Guide
98
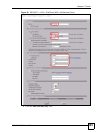
Network Policy
Setting
Local Network
Starting IP Address This is a (static) IP address on the LAN behind your ZyWALL.
Ending IP Address/
Subnet Mask
When the local network is configured for a single IP address, this field is N/A.
When the local network is configured for a range IP address, this is the end
(static) IP address, in a range of computers on the LAN behind your ZyWALL.
When the local network is configured for a subnet, this is a subnet mask on the
LAN behind your ZyWALL.
Remote Network
Starting IP Address This is a (static) IP address on the network behind the remote IPSec router.
Ending IP Address/
Subnet Mask
When the remote network is configured for a single IP address, this field is N/A.
When the remote network is configured for a range IP address, this is the end
(static) IP address, in a range of computers on the network behind the remote
IPSec router. When the remote network is configured for a subnet, this is a
subnet mask on the network behind the remote IPSec router.
IKE Tunnel Setting
(IKE Phase 1)
Negotiation Mode This shows Main Mode or Aggressive Mode. Multiple SAs connecting through
a secure gateway must have the same negotiation mode.
Encryption
Algorithm
This is the method of data encryption. Options can be DES, 3DES or AES.
Authentication
Algorithm
MD5 (Message Digest 5) and SHA1 (Secure Hash Algorithm) are hash
algorithms used to authenticate packet data.
Key Group This is the key group you chose for phase 1 IKE setup.
SA Life Time
(Seconds)
This is the length of time before an IKE SA automatically renegotiates.
Pre-Shared Key This is a pre-shared key identifying a communicating party during a phase 1 IKE
negotiation.
IPSec Setting (IKE
Phase 2)
Encapsulation Mode This shows Tunnel mode or Transport mode.
IPSec Protocol ESP or AH are the security protocols used for an SA.
Encryption
Algorithm
This is the method of data encryption. Options can be DES, 3DES, AES or
NULL.
Authentication
Algorithm
MD5 (Message Digest 5) and SHA1 (Secure Hash Algorithm) are hash
algorithms used to authenticate packet data.
SA Life Time
(Seconds)
This is the length of time before an IKE SA automatically renegotiates.
Perfect Forward
Secret (PFS)
Perfect Forward Secret (PFS) is disabled (None) by default in phase 2 IPSec
SA setup. Otherwise, DH1 or DH2 are selected to enable PFS.
Back Click Back to return to the previous screen.
Finish Click Finish to complete and save the wizard setup.
Table 20 VPN Wizard: VPN Status (continued)
LABEL DESCRIPTION