74 AT-WR4500 Series - IEEE 802.11abgh Outdoor Wireless Routers
RouterOS v3 Configuration and User Guide
On the AP in default or in your own made profile as an encryption algorithm choose wpa-psk. Specify
the pre-shared-key, wpa-unicast-ciphers and wpa-group-cipher
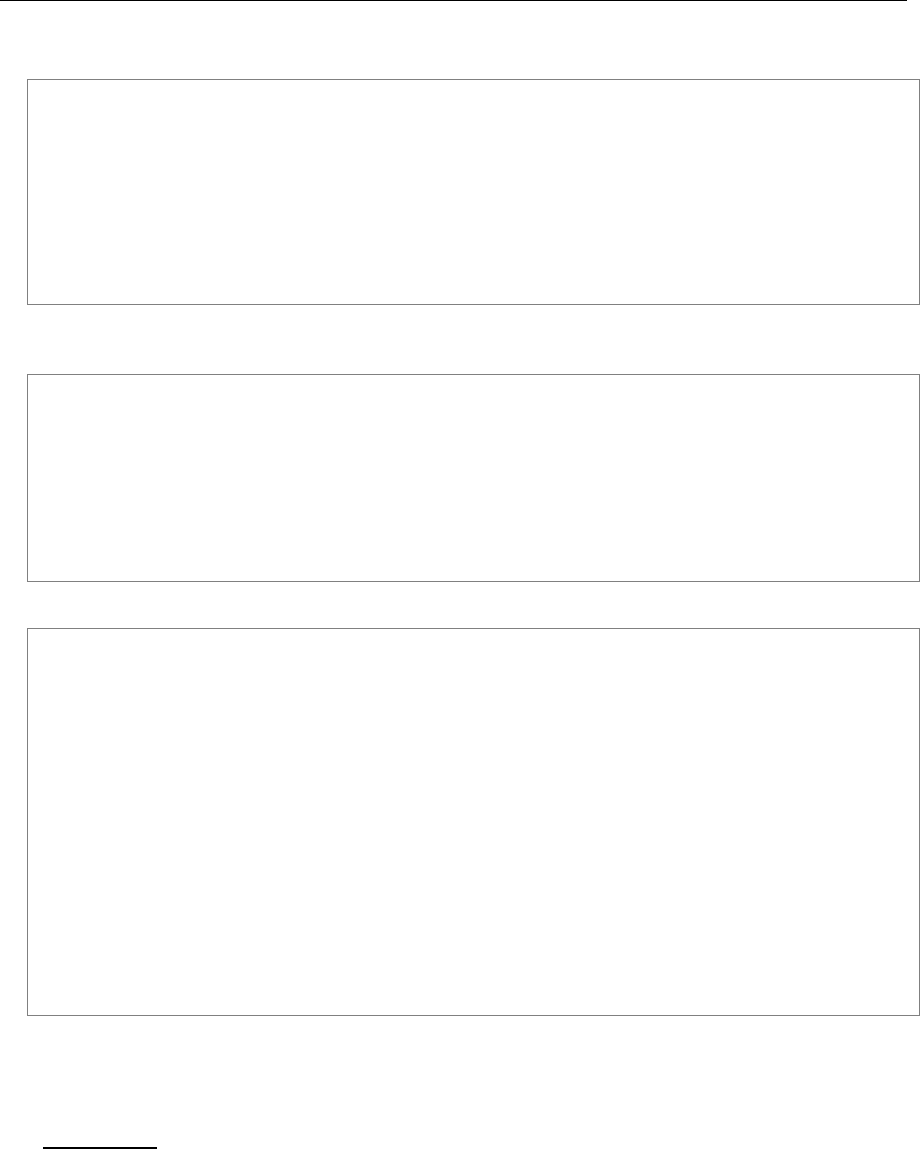
[admin@WPA_AP] interface wireless security-profiles> set default mode=wpa-psk\
\... pre-shared-key=1234567890 wpa-unicast-ciphers=aes-ccm,tkip wpa-group-ciphers=aes-
ccm,tkip
[admin@WPA_AP] interface wireless security-profiles> pr
0 name="default" mode=wpa-psk wpa-unicast-ciphers=tkip,aes-ccm
wpa-group-ciphers=tkip,aes-ccm pre-shared-key="1234567890"
static-algo-0=none static-key-0="" static-algo-1=none static-key-1=""
static-algo-2=none static-key-2="" static-algo-3=none static-key-3=""
static-transmit-key=key-0 static-sta-private-algo=none
static-sta-private-key="" radius-mac-authentication=no group-key-update=5m
[admin@WPA_AP] interface wireless security-profiles>
On the Client do the same. Encryption algorithm, wpa-group-cipher and pre-shared-key must be the
same as specified on AP, wpa-unicast-cipher must be one of the ciphers supported by Access Point
[admin@WPA_Station] interface wireless security-profiles> set default mode=wpa-psk\
\... pre-shared-key=1234567890 wpa-unicast-ciphers=tkip wpa-group-ciphers=aes-ccm,tkip
[admin@WPA_Station] interface wireless security-profiles> pr
0 name="default" mode=wpa-psk wpa-unicast-ciphers=tkip
wpa-group-ciphers=tkip,aes-ccm pre-shared-key="1234567890"
static-algo-0=none static-key-0="" static-algo-1=none static-key-1=""
static-algo-2=none static-key-2="" static-algo-3=none static-key-3=""
static-transmit-key=key-0 static-sta-private-algo=none
static-sta-private-key="" radius-mac-authentication=no group-key-update=5m
[admin@WPA_Station] interface wireless security-profiles>
Test the link between Access point and the client
[admin@WPA_Station] interface wireless > print
Flags: X - disabled, R - running
0 R name="wlan1" mtu=1500 mac-address=00:0B:6B:35:E5:5C arp=enabled
disable-running-check=no interface-type=Atheros AR5213
radio-name="000B6B35E55C" mode=station ssid="AT-WR4500" area=""
frequency-mode=superchannel country=no_country_set antenna-gain=0
frequency=5180 band=5ghz scan-list=default rate-set=default
supported-rates-b=1Mbps,2Mbps,5.5Mbps,11Mbps
supported-rates-a/g=6Mbps,9Mbps,12Mbps,18Mbps,24Mbps,36Mbps,48Mbps,
54Mbps
basic-rates-b=1Mbps basic-rates-a/g=6Mbps max-station-count=2007
ack-timeout=dynamic tx-power-mode=default noise-floor-threshold=default
periodic-calibration=default burst-time=disabled dfs-mode=none
antenna-mode=ant-a wds-mode=disabled wds-default-bridge=none
wds-ignore-ssid=no update-stats-interval=disabled
default-authentication=yes default-forwarding=yes default-ap-tx-limit=0
default-client-tx-limit=0 hide-ssid=no security-profile=default
disconnect-timeout=3s on-fail-retry-time=100ms preamble-mode=both
compression=no allow-sharedkey=no
[admin@WPA_Station] interface wireless >
4.3.22 Troubleshooting
Description
If I use WDS and DFS, the routers do not connect to each other!
As the WDS routers must operate at the same frequency, it is very probable that DFS will not select the
frequency that is used by the peer router.
RouterOS does not send any traffic through Cisco Wireless Access Point or Wireless Bridge
If you use CISCO/Aironet Wireless Ethernet Bridge or Access Point, you should set the
Configuration/Radio/I80211/Extended (Allow proprietary extensions) to off, and the
Configuration/Radio/I80211/Extended/Encapsulation (Default encapsulation method) to RFC1042. If left
to the default on and 802.1H, respectively, you won't be able to pass traffic through the bridge.


















