96
Enhancements in Release F.04.08
Configuring Secure Shell (SSH)
b. Uses MD5 to create a hash version of this information.
c. Returns the hash version to the switch.
7. The switch computes its own hash version of the data in step 6 and compares it to the client’s
hash version. If they match, then the client is authenticated. Otherwise, the client is denied
access.
Using client public-key authentication requires these steps:
1. Generate a public/private key pair for each client you want to have SSH access to the switch.
This can be a separate key for each client or the same key copied to several clients.
2. Copy the public key for each client into a client-public-key text file. (For the SSHv1 application
used in the switch, this must be in the ASCII format (without PEM or any other encoding). If
you are using an SSHv2 client application that creates its public key in a PEM-encoded ASCII
string, you will need to convert the client’s public key to a non-encoded version. Refer to the
documentation provided with the application.)
3. Use copy tftp to copy the client-public-key file into the switch. Note that the switch can hold only
one of these files. If there is already a client-public-key file in the switch and you copy another
one into the switch, the second file replaces the first file.
4. Use the aaa authentication ssh command to enable client public-key authentication.
To Create a Client-Public-Key Text File. These steps describe how to copy client-public-keys
into the switch for RSA challenge-response authentication, and require an understanding of how to
use your SSH client application.
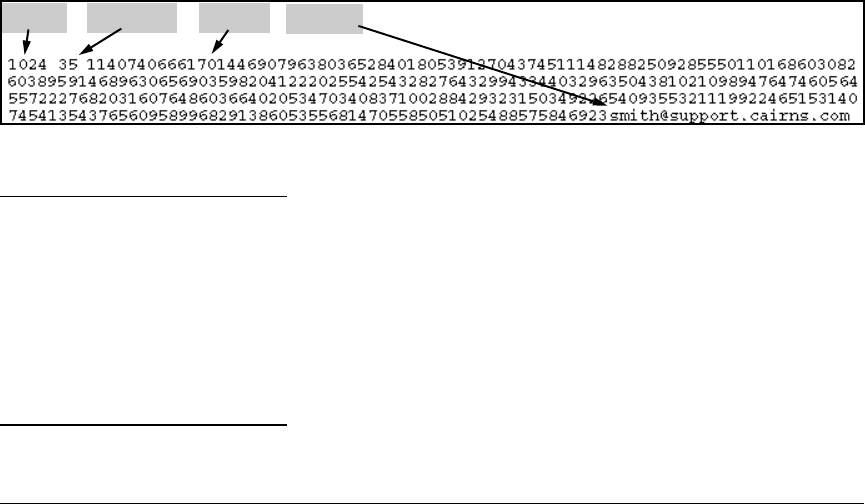
Figure 39. Example of a Client Public Key
Notes
Comments in public key files, such as smith@support.cairns.com in figure 39, may appear in
a SSH client application’s generated public key. While such comments may help to distinguish one
key from another, they do not pose any restriction on the use of a key by multiple clients and/or users.
Public key illustrations such as the key shown in figure 39 usually include line breaks as a method
for showing the whole key. However, in practice, line breaks in a public key will cause errors resulting
in authentication failure.
Bit Size Public Index
Modulus
Comment


















