67
Enhancements in Release F.05.05 through F.05.70
Enhancements in Release F.05.05 through F.05.60
How RADIUS/802.1X Authentication Affects VLAN Operation
Static VLAN Requirement. RADIUS authentication for an 802.1X client on a given port can include
a (static) VLAN requirement. (Refer to the documentation provided with your RADIUS application.)
The static VLAN to which a RADIUS server assigns a client must already exist on the switch. If it
does not exist or is a dynamic VLAN (created by GVRP), authentication fails. Also, for the session to
proceed, the port must be an untagged member of the required VLAN. If it is not, the switch
temporarily reassigns the port as described below.
If the Port Used by the Client Is Not Configured as an Untagged Member of the Required
Static VLAN: When a client is authenticated on port “N”, if port “N” is not already configured as an
untagged member of the static VLAN specified by the RADIUS server, then the switch temporarily
assigns port “N” as an untagged member of the required VLAN (for the duration of the 802.1X session).
At the same time, if port “N” is already configured as an untagged member of another VLAN, port
“N” loses access to that other VLAN for the duration of the session. (This is because a port can be
an untagged member of only one VLAN at a time.)
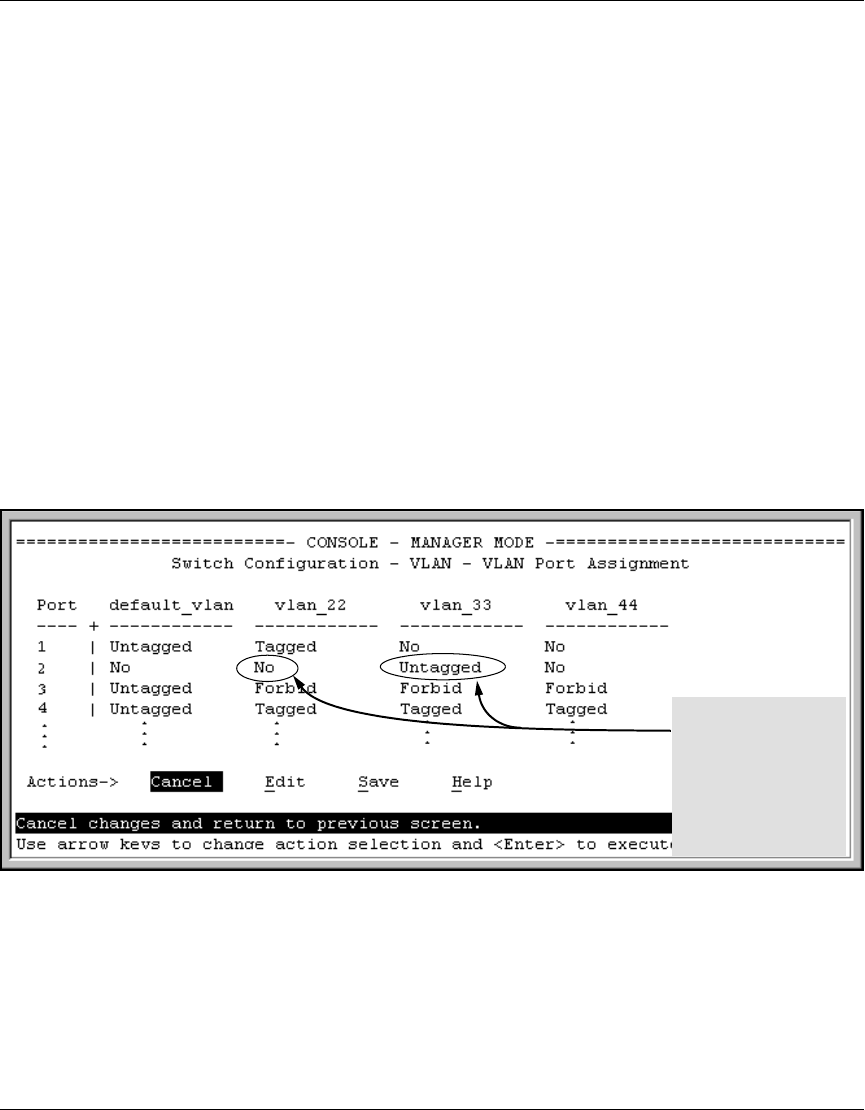
For example, suppose that a RADIUS-authenticated, 802.1X-aware client on port 2 requires access
to VLAN 22, but VLAN 22 is configured for no access on port 2, and VLAN 33 is configured as untagged
on port 2:
Figure 16. Example of an Active VLAN Configuration
In figure 16, if RADIUS authorizes an 802.1X client on port 2 with the requirement that the client use
VLAN 22, then:
■ VLAN 22 becomes available as Untagged on port 2 for the duration of the session.
Scenario: An authorized
802.1X client requires
access to VLAN 22 from
port 2. However, access
to VLAN 22 is blocked (not
untagged or tagged) on
port 2 and VLAN 33 is
untagged on port 2.


















