78
Enhancements in Release F.04.08
Configuring Secure Shell (SSH)
Configuring Secure Shell (SSH)
The Series 2500 switches use Secure Shell version 1 (SSHv1) to provide remote access to management
functions on the switches via encrypted paths between the switch and management station clients
capable of SSHv1 operation. (The switches can be authenticated by SSHv2 clients that support
SSHv1.) However, to use the reverse option—authenticating an SSHv2 user to the switch—you must
have a method for converting the SSHv2 PEM public-key format to non-encoded ASCII. Refer to "PEM
(Privacy Enhanced Mode)" on page 80.
SSH provides Telnet-like functions but, unlike Telnet, SSH provides encrypted, authenticated trans-
actions. The authentication types include:
■ Client public-key authentication
■ Switch SSH and user password authentication
Client Public Key Authentication (Login/Operator Level) with User Password
Authentication (Enable/Manager Level). This option uses one or more public keys (from
clients) that must be stored on the switch. Only a client with a private key that matches a stored
public key can gain access to the switch. (The same private key can be stored on one or more clients.)
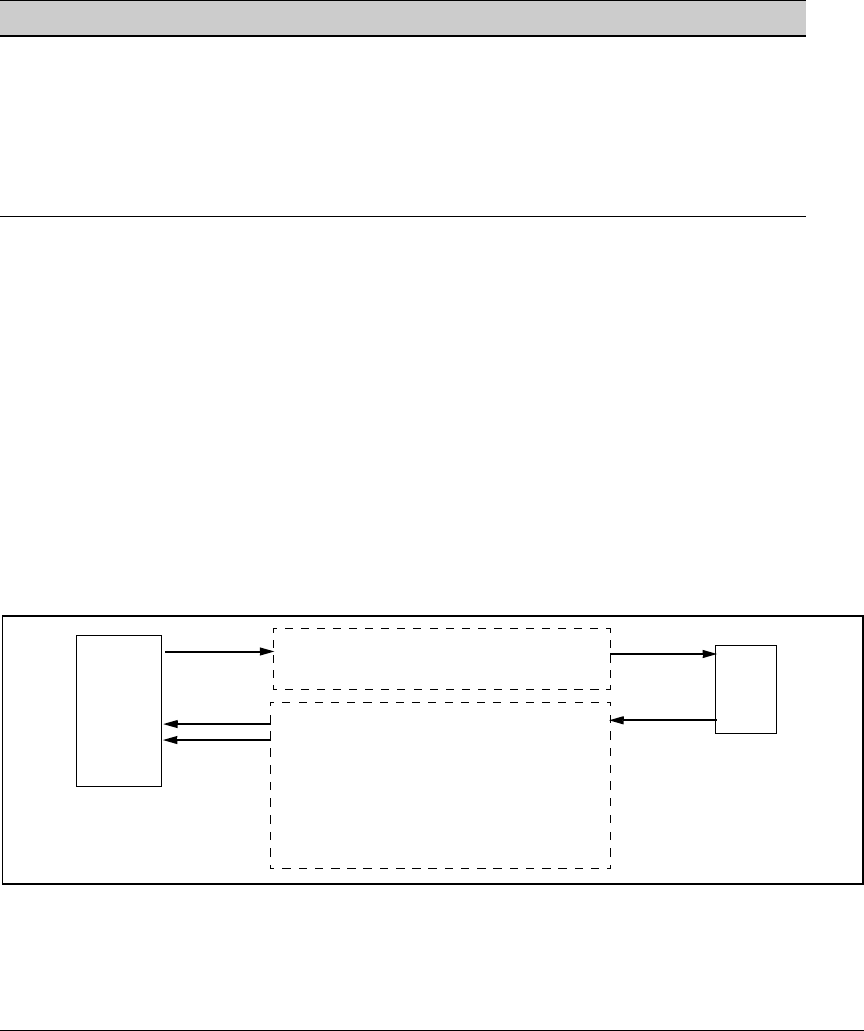
Figure 26. Client Public Key Authentication Model
Feature Default Menu CLI Web
Generating a public/private key pair on the switch No n/a page 85 n/a
Using the switch’s public key n/a n/a page 87 n/a
Enabling SSH Disabled n/a page 89 n/a
Enabling client public-key authentication Disabled n/a pages 92, 95 n/a
Enabling user authentication Disabled n/a page 92 n/a
Series 2500
Switch
(SSH
Server)
1.Switch-to-Client SSH authentication
2.Client-to-Switch (login rsa) authentication
3.User-to-Switch (enable password) authentica
tion options:
– Local
– TACACS+
–RADIUS
–None
SSH
Client
Work-
Station


















