Psion Teklogix 9160 G2 Wireless Gateway User Manual 59
Chapter 6: Managing Access Points & Clusters
Intra-Cluster Security
6.3.7 Intra-Cluster Security
For purposes of ease-of-use, the clustering component is designed to let new devices
join a cluster without strong authentication. However, communications of all data
between access points in a cluster is protected against casual eavesdropping using
Secure Sockets Layer (SSL). The assumption is that the private wired network to
which the devices are connected is secure. Both the cluster configuration file and the
user database are transmitted among access points using SSL.
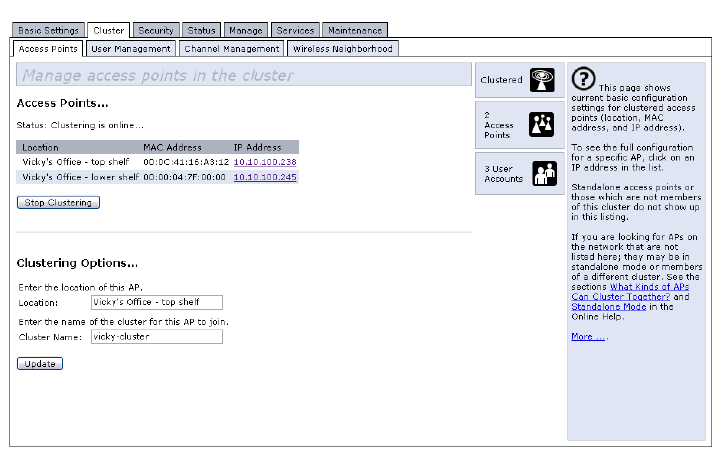
6.4 Understanding Access Point Settings
The Access Points tab provides information about all access points in the cluster.
From this tab, you can view location descriptions, MAC addresses, IP addresses,
enable (activate) or disable (deactivate) clustered access points, and remove access
points from the cluster. You can also modify the location description for an access
point. The IP address links provide a way to navigate to configuration settings and
data on an access point.
Standalone access points (those which are not members of the cluster) are not shown
on this page.
Table 6.1 describes the access point settings and information display in detail.


















