CLI Mode-based Topology Command
Reference
perform a save.
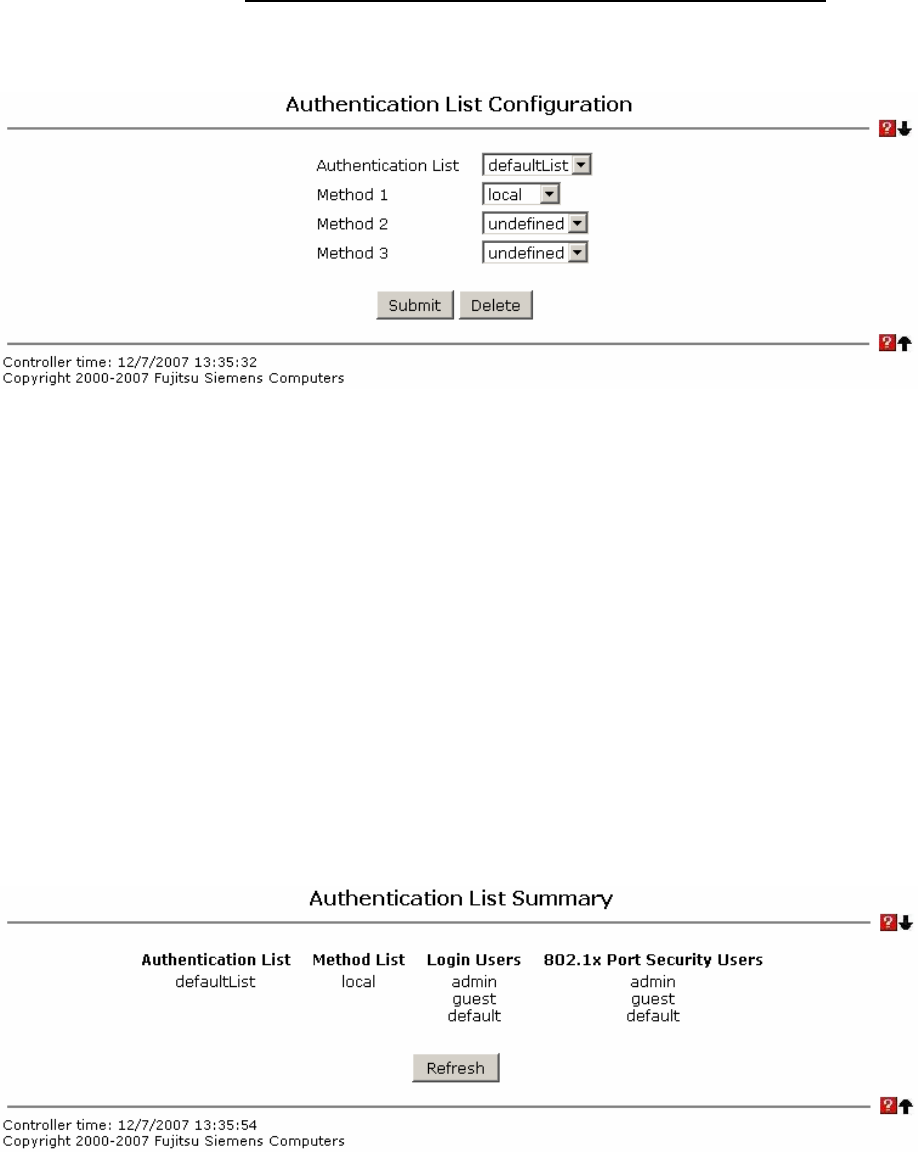
6.2.1.3.3 Viewing Authentication List Summary Page
Non-Configurable Data
Authentication List - Identifies the authentication login list summarized in this row.
Method List - The ordered list of methods configured for this login list.
Login Users - The users you assigned to this login list on the User Login Configuration
screen. This list is used to authenticate the users for system login access.
802.1x Port Security Users The users you assigned to this login list on the Port Access
Control User Login Configuration screen - This list is used to authenticate the users for
port access, using the IEEE 802.1x protocol.
Command Buttons
Refresh - Update the information on the page.
6.2.1.3.4 Defining User Login Page
Note: This page provides a user account (from those already created) to be added into
the Authentication List.
Each configured user is assigned to a login list that specifies how the user should be
authenticated when attempting to access the IBP or a port on the IBP. After creating a new user
account on the User Account screen, you should assign that user to a login list for the IBP
using this screen and, if necessary, to a login list for the ports using the Port Access Control


















