6-125
Configuring the Switch
Configuring and Monitoring Port Security
Configuring the Switch
Reading and Resetting Intrusion Alarms
When an attempted security violation occurs on a port configured for Port
Security, the port drops the packets it receives from the unauthorized device.
Notice of Security Violations
When a security violation occurs on a port configured for Port Security, the
switch responds in the following ways to notify you:
■ The switch sets an alert flag for that port. This flag remains until:
• You use either the console or web browser interface to reset the flag.
• The switch is reset to its factory default configuration.
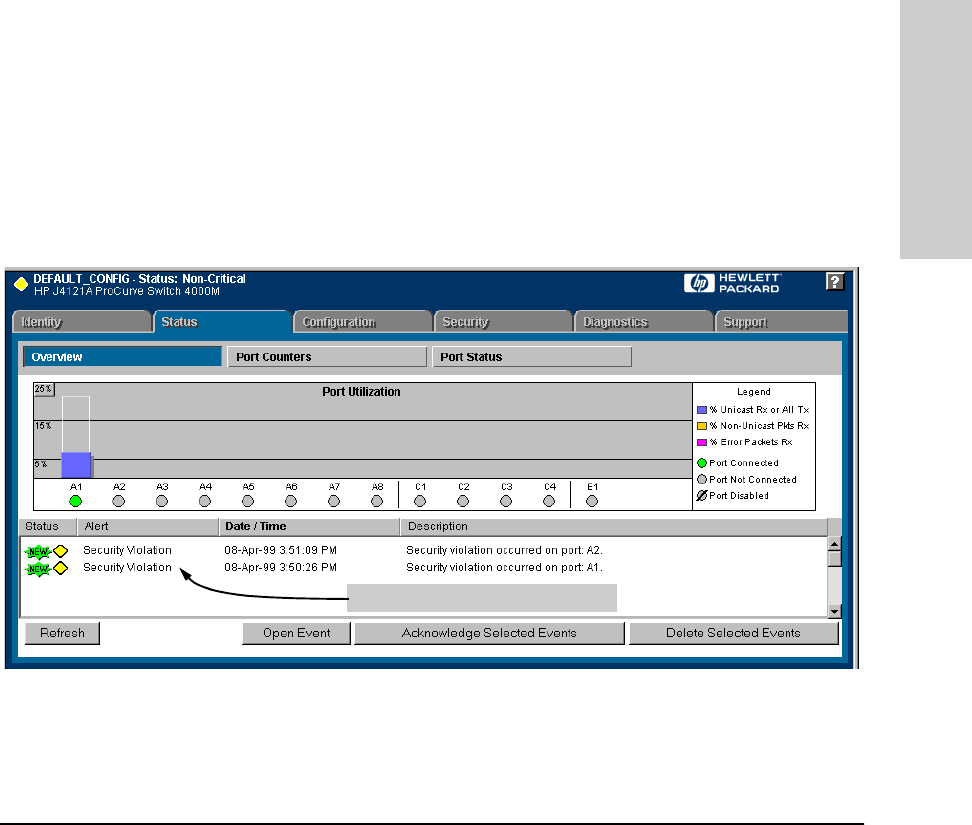
■ The web browser and console interfaces notify you of the intrusion.
• In the web browser interface:
– The Alert Log displays a Security Violation entry, with the system
date and time, and the port on which the violation occurred
(figure 6-81, below).
– The Intrusion Log lists the port number, the MAC address of
the intruding device, and the system time and date when the
intrusion occurred (figure 6-82 on page 6-126).
.
Figure 6-81. Example of Security Violation Entries in the Alert Log of the Switch’s
Web Browser Interface
Security Violation Entries in the Alert Log


















