6-127
Configuring the Switch
Configuring and Monitoring Port Security
Configuring the Switch
Figure 6-83. Example of the Switch Console Event Log with Security Violation
Entries
• The Intrusion Alert column in the console’s Port Status screen dis-
plays
Yes for the port on which the violation occurred (figure 6-84,
below).
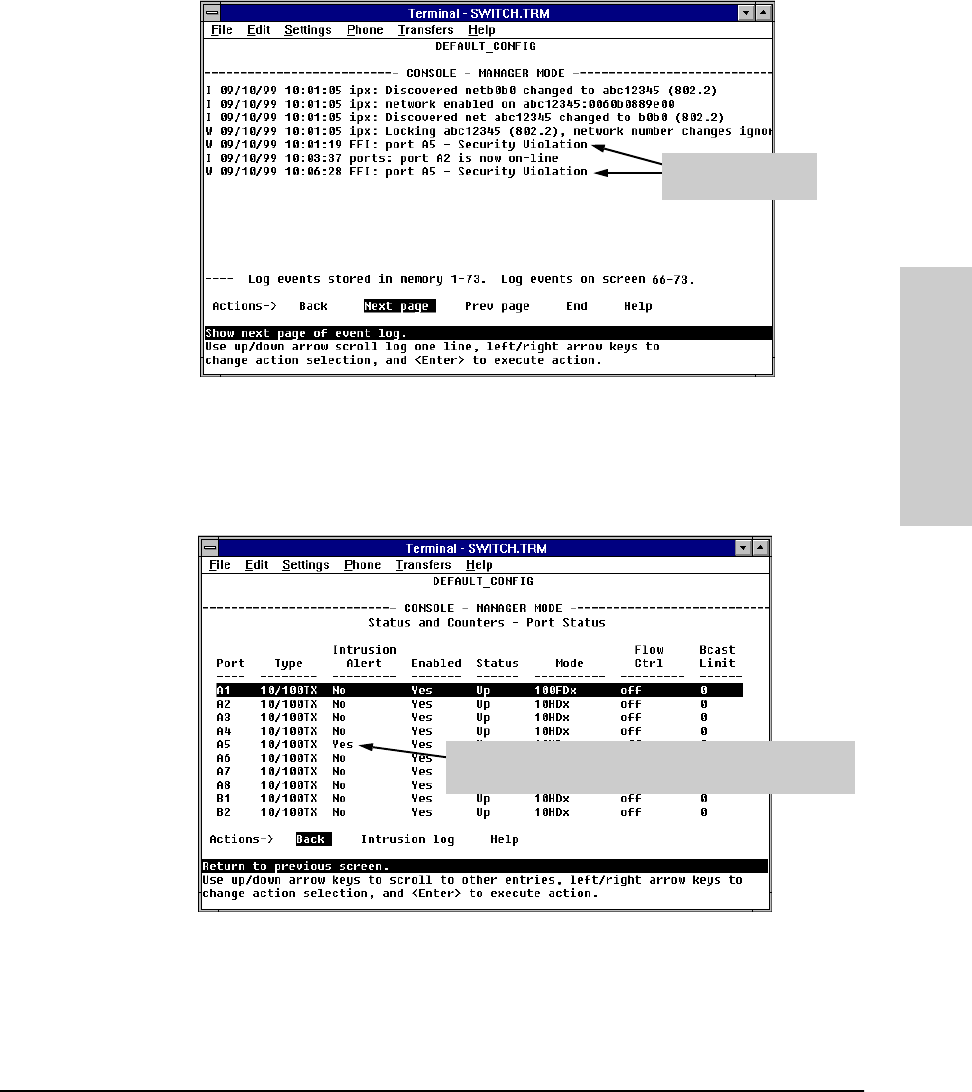
Figure 6-84. Example of Port Status Screen with Intrusion Alert on Port A5
• The console’s Intrusion Log lists the port number, the MAC address
of the intruding device, and the system time and date when the
intrusion occurred (figure 6-85, below).
Examples of Security
Violation entries.
Intrusion alert indicated on Port A5. After you reset the alert flag
(in the Intrusion Log screen, below), this entry changes to
No.


















