Chapter 5 Operation Procedures
III-2
Chapter 5 Operation Procedures
5
5
5
.
.
.
1
1
1
I
I
I
n
n
n
i
i
i
t
t
t
i
i
i
a
a
a
l
l
l
I
I
I
n
n
n
s
s
s
t
t
t
a
a
a
l
l
l
l
l
l
a
a
a
t
t
t
i
i
i
o
o
o
n
n
n
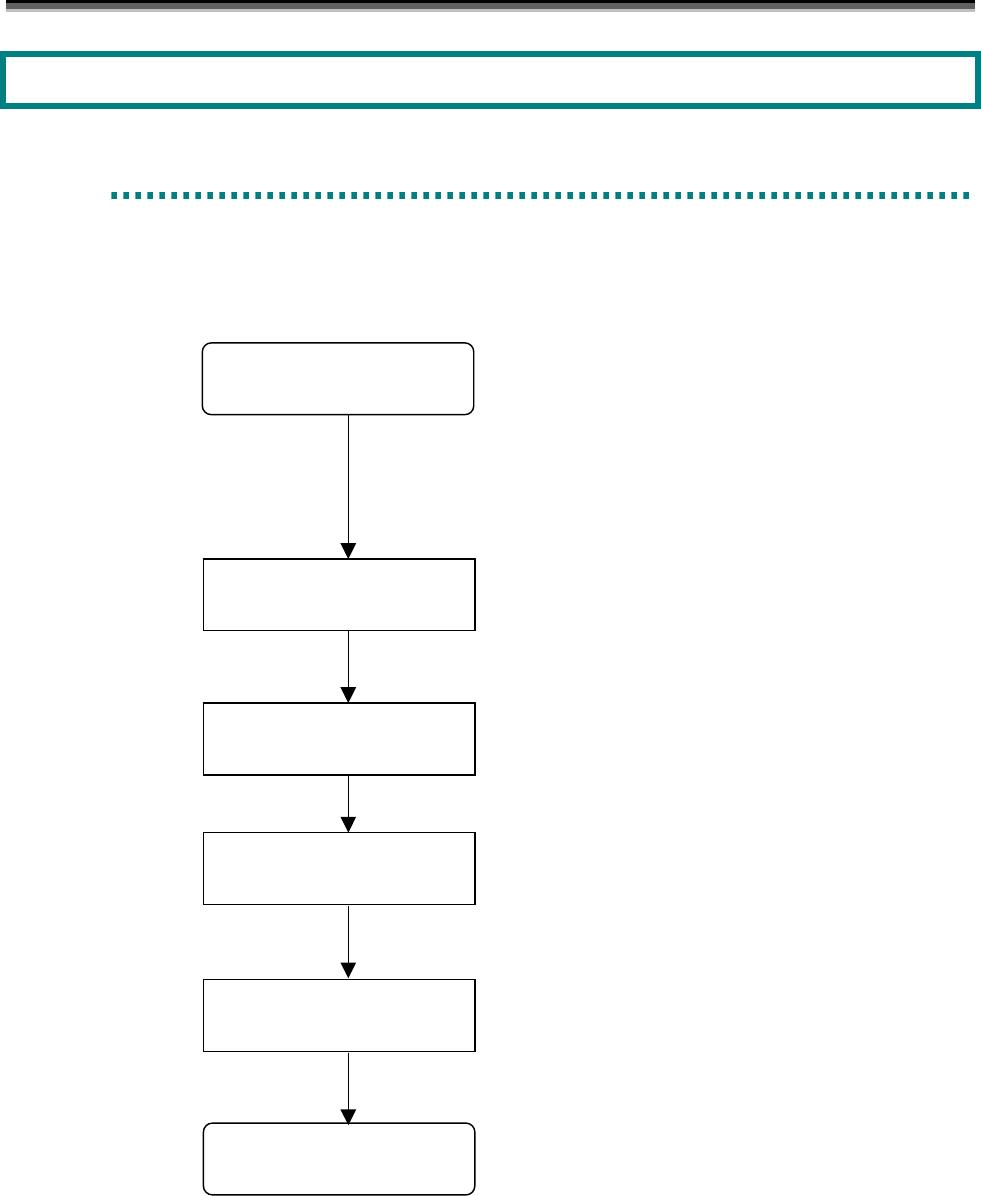
When initially installing a system and a disk array, make the settings basically in accordance with the following
procedure.
Execute the following work while referring to the “User’s
Manual” or “User’s Manual (UNIX)” in accordance with
your OS.
• Install the iSM.
• Set the target disk array as a monitoring target.
• Set the user information.
If necessary, set a Disk Array. (For details, refer to
5.1.2 “Setting a Disk Array”.)
Bind a pool or RANK. (For details, refer to 5.1.3
“Binding a Pool or RANK”.)
Bind a logical disk. (For details, refer to 5.1.4 “Binding
a Logical Disk”.)
Set a nickname of the logical disk. (For details, refer to
5.1.5 “Setting a Logical Disk Nickname”.)
If necessary, newly install the Access Control. (For
details, refer to 5.1.6 “Installing the Access Control”.)
Set a Disk Array
Bind a Pool or RANK
Bind a Logical Disk
Set a Logical Disk Nickname
Install the Access Control
Set the Storage Manger


















