9: Services
Spider™ and SpiderDuo® KVM-over-IP Device User Guide 87
Certificate
The Spider device uses the Secure Socket Layer (SSL) protocol for any encrypted network traffic
between itself and a connected client. During the connection establishment the Spider device has
to expose its identity to a client using a cryptographic certificate. Upon leaving the factory this
certificate and the underlying secret key is the same for all Spider devices and will not match the
network configuration where it is installed. The certificate’s underlying secret key is also used for
securing the SSL handshake. Leaving the default certificate unmodified is all right in most
circumstances and is necessary only if the network facility is vulnerable to man-in-the-middle
attack.
It is possible to generate and install a new base64 x.509 certificate that is unique for a particular
Spider device. The Spider device is able to generate a new cryptographic key and the associated
Certificate Signing Request (CSR) that needs to be certified by a certification authority (CA).
To create and install an SSL certificate, perform the following steps.
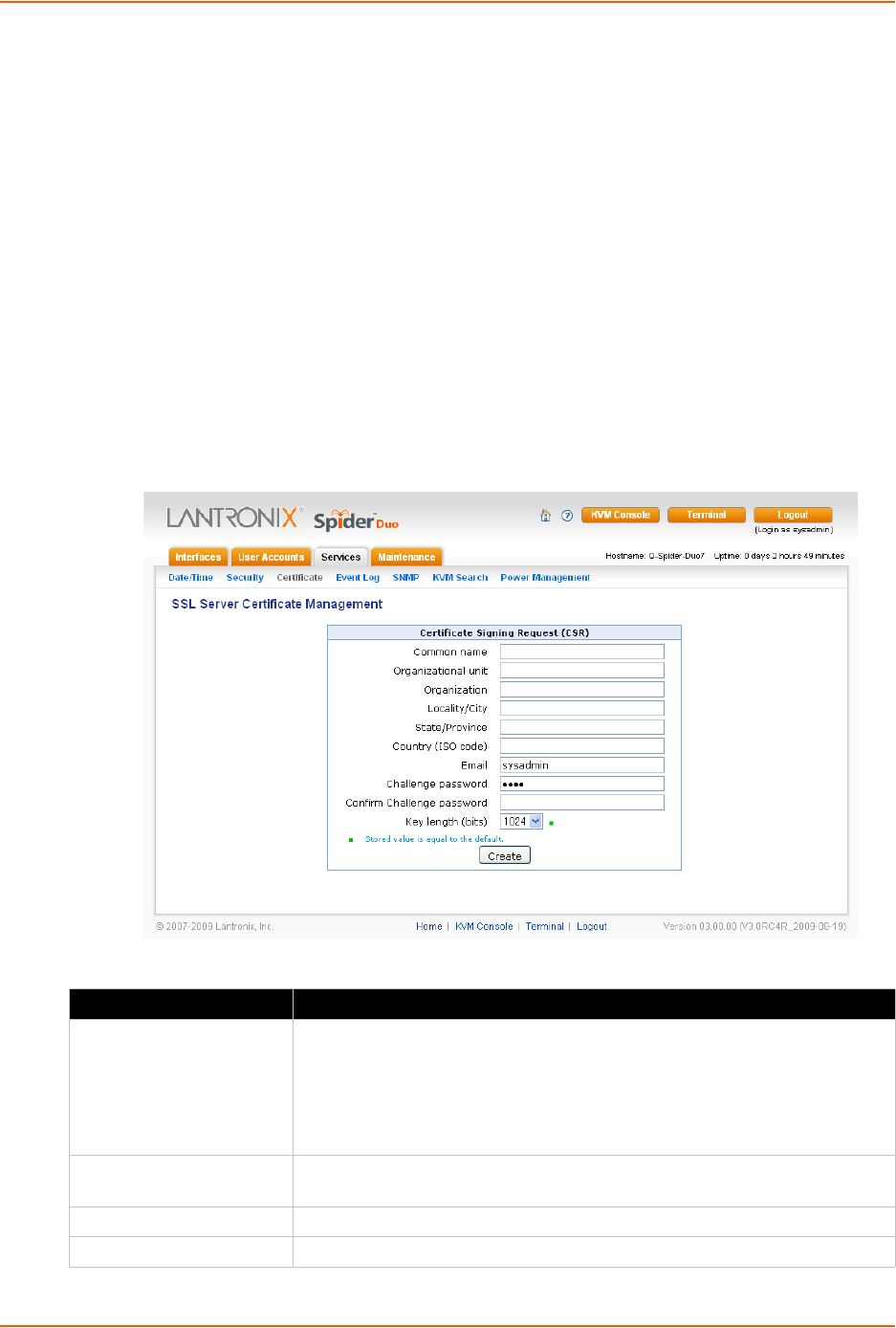
1. Click Services > Certificate. The Certificate Signing Request page displays.
Figure 9-4 Certificate Signing Request Page
2. Modify the following fields.
Field Description
Common name The network name of the Spider device once it is installed in the user’s
network (usually the fully qualified domain name). It is identical to the name
that is used to access the Spider device with a web browser without the
prefix http://. In case the name given here and the actual network name
differ, the browser will pop up a security warning when the Spider device is
accessed using HTTPS.
Organizational unit This field specifies to the department within an organization to which the
Spider device belongs.
Organization The name of the organization to which the Spider device belongs.
Locality/City The city where the organization is located.


















