Manage Users, Authentication, and VPN Certificates
288
ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N
Except in the case of IPSec VPN users, when you create a user account, you need to specify
a group. When you create a group, you need to specify a domain.
The following table summarizes the external authentication protocols and methods that the
wireless VP
N firewall supports.
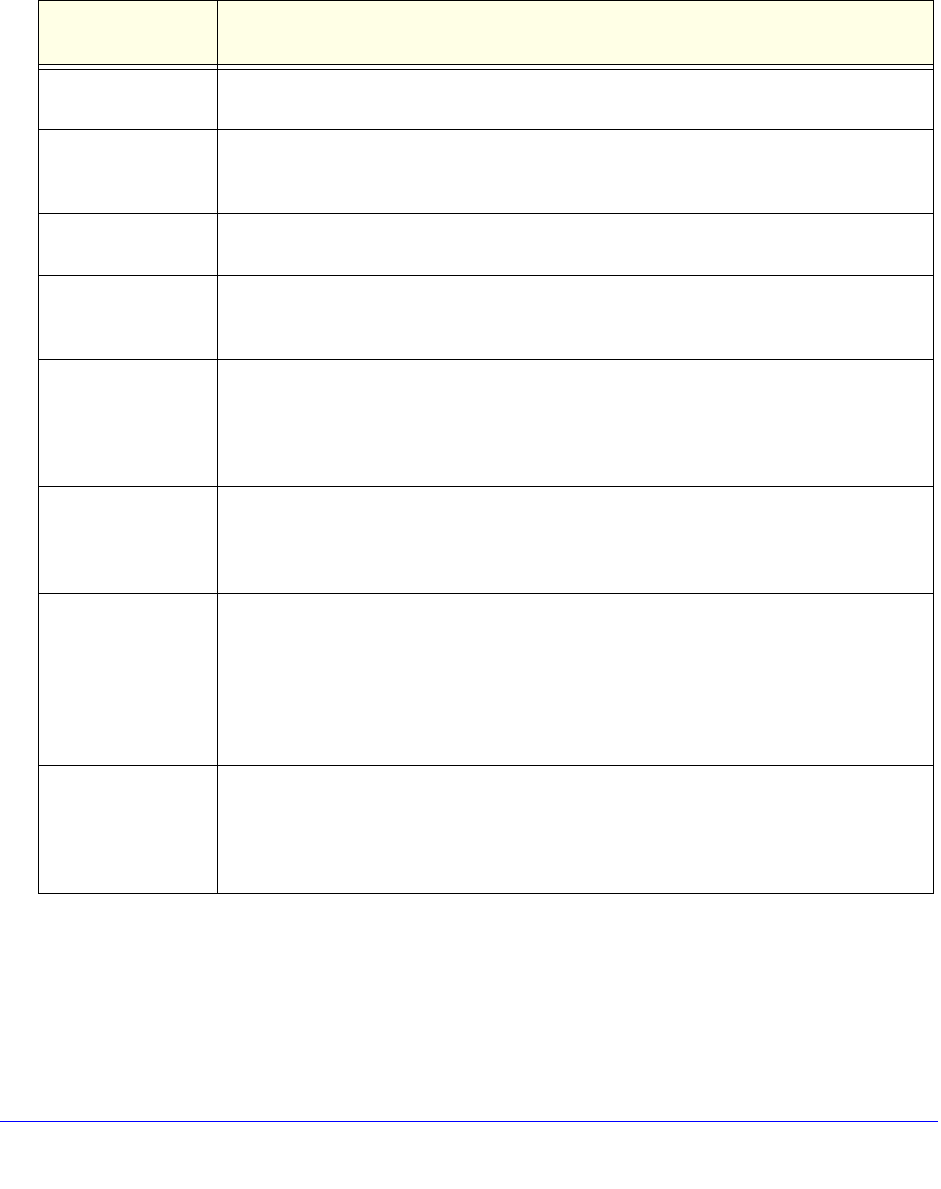
Table 70. External authentication protocols and methods
Authentication
Protocol or Method
Description
PAP Password Authentication Protocol (PAP) is a simp
le protocol in which the client sends a
password in clear text.
CHAP Challenge Handshake Authentication Protocol
(CHAP) executes a three-way handshake
in which the client and server trade challenge messages, each responding with a hash of
the other’s challenge message that is calculated using a shared secret value.
RADIUS A network-validated PAP or CHAP password-based
authentication method that functions
with Remote Authentication Dial In User Service (RADIUS).
MIAS A network-validated PAP or CHAP password-based
authentication method that functions
with Microsoft Internet Authentication Service (MIAS), which is a component of Microsoft
Windows 2003 Server.
WiKID WiKID Systems is a PAP or CHAP key-based two-facto
r authentication method that
functions with public key cryptography. The client sends an encrypted PIN to the WiKID
server and receives a one-time passcode with a short expiration period. The client logs in
with the passcode. See Appendix B, Two-Factor Authentication, for more on WiKID
authentication.
NT Domain A network-validated domain-based authentication me
thod that functions with a Microsoft
Windows NT Domain authentication server. This authentication method has been
superseded by Microsoft Active Directory authentication but is supported to authenticate
legacy Windows clients.
Active Directory A network-validated domain-based authentication me
thod that functions with a Microsoft
Active Directory authentication server. Microsoft Active Directory authentication servers
support a group and user structure. Because the Active Directory supports a multilevel
hierarchy (for example, groups or organizational units), this information can be queried to
provide specific group policies or bookmarks based on Active Directory attributes.
Note: A Microsoft Active Directory database
uses an LDAP organization schema.
LDAP A network-validated domain-base
d authentication method that functions with a
Lightweight Directory Access Protocol (LDAP) authentication server. LDAP is a standard
for querying and updating a directory. Because LDAP supports a multilevel hierarchy (for
example, groups or organizational units), this information can be queried to provide
specific group policies or bookmarks based on LDAP attributes.


















