Chapter 13 VoIP Trunking
P-2302HWUDL-P1 Series User’s Guide
162
Other settings controlled by the auto attendant include a time limit to decide whether you want
to forward a call from the ZyXEL Device or call the phone directly connected to the ZyXEL
Device. When you call into your ZyXEL Device you can request to forward a call to another
phone number simply by dialing that number. If you don’t dial any number within a specified
time limit (for example 5 seconds) then the phone directly connected to the ZyXEL Device
rings. It also controls the time limit you have between dialing digits of a phone number.
13.2.2 Peer Call Authentication
VoIP devices can make peer calls to each other by using the IP address instead of a SIP
number to establish a call. The advantage of this is that you do not need to pay a VoIP service
provider. VoIP devices that connect using an IP address are referred to here as peer devices. A
local peer device is where the VoIP call originates and a remote peer device is where the VoIP
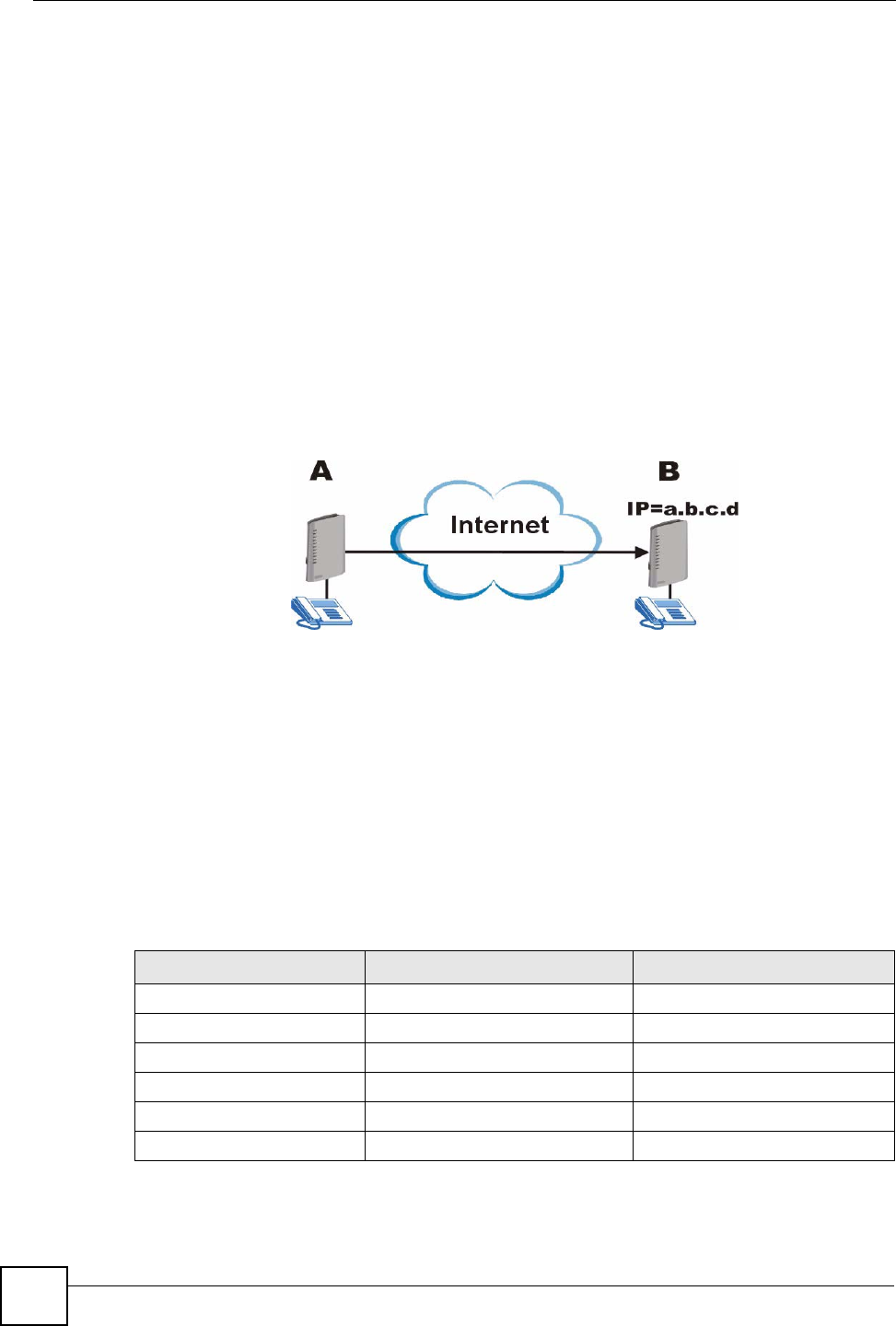
call ends. In the following figure, local peer device (A) connects to a remote peer device (B)
via the IP address of B.
Figure 87 Peer Devices Connecting
A peer-to-peer call doesn’t require any authentication, however, authentication is required
when you request the remote peer device to forward a call. The remote peer device has a list of
accounts, each consisting of a username and password, which are allowed to use the remote
peer device to forward calls. These accounts make up an incoming authentication list.
The local peer device has a corresponding list of outgoing authentication accounts. These
accounts consist of the IP address of a remote peer device, the port number to communicate
over as well as a username and password to use for authentication. An outgoing authentication
account must match an incoming authentication account’s username and password in order for
the remote device to forward calls. The following table shows example entries for incoming
and outgoing authentication. The bolded entries must match in order for authentication
between two peer devices to occur.
Table 71 Matching Incoming and Outgoing Authentication
ACCOUNT DETAILS LOCAL PEER DEVICE REMOTE PEER DEVICE
Outgoing Authentication
Username localDeviceA localDeviceB
Password passwordA passwordB
Incoming Authentication
Username userone localDeviceA
Password userpassword passwordA


















