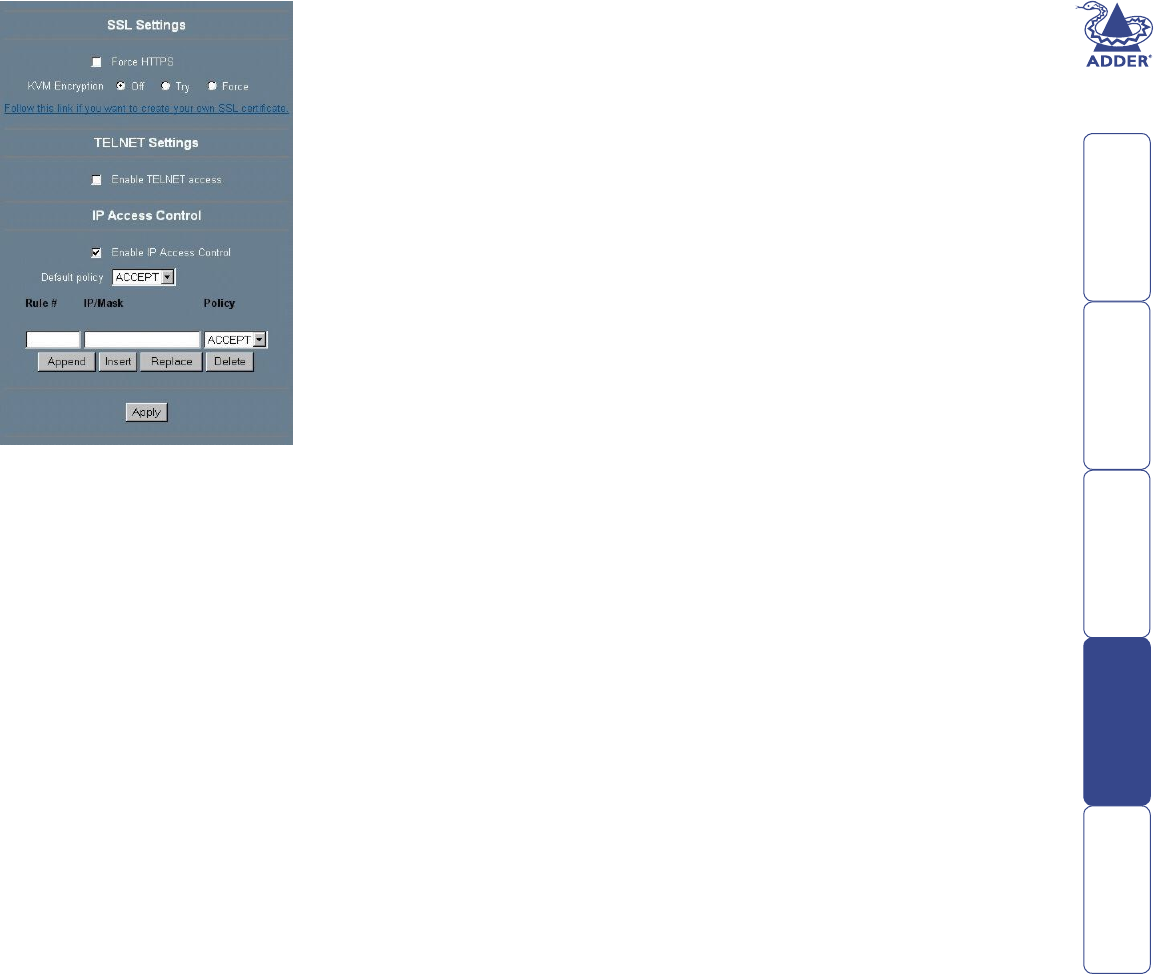
56
Rule Number
This should contain the number of a rule for which the following commands will
apply. This eld will be ignored, in case of appending a new rule.
IP/Mask
Species the IP address or IP address range for which the rule applies.
Examples (the number concatenated to an IP address with a ‘/’ is the number of
valid bits that will be used of the given IP address):
192.168.1.22/32 matches the IP Address 192.168.1.22
192.168.1.0/24 matches all IP packets with source addresses from 192.168.1.0
to 192.168.1.255
0.0.0.0/0 matches any IP packet
Policy
The policy determines what to do with matching packets. They can be accepted
or dropped.
Note: The order of the rules is important. The rules are checked in ascending
order until a rule matches. All the rules below the matching one will be ignored.
The default policy applies if no match has been found.
Appending a rule
Enter the IP/Mask and set the policy. Finally, press ‘Append’.
Inserting a rule
Enter the rule number, the IP/Mask and set the policy. Finally, press ‘Insert’.
Replacing a rule
Enter the rule number, the IP/Mask and set the policy. Finally, press ‘Replace’.
Deleting a rule
Enter the rule number and press ‘Delete’.
Security Settings
SSL Settings
Force HTTPS
If this option is enabled access to the
Web front-end is only possible using an
HTTPS connection. The SmartView World
won’t listen on the HTTP port for incoming
connections.
KVM encryption
This option controls the encryption of the
RFB protocol, the protocol used by the
Remote Console to transmit the screen data
to the administrator machine and keyboard
and mouse data back to the host.
If set to ‘Off’ no encryption will be used.
If set to ‘Try’ the applet tries to make an
encrypted connection. In case connection
establishment fails for any reason an
unencrypted connection will be used.
If set to ‘Force’ the applet tries to make an encrypted connection. An error will
be reported in case connection establishment fails.
Telnet Settings
Enable Telnet access
If this option is enabled, access over Telnet client is possible. For higher security
we recommend to disable Telnet access.
IP Access Control
This section explains the settings related to IP access control. It is used to limit
access to a distinguished number of clients only. These clients will be identied
by their IP address, from which they are trying to build up a connection.
Note: The IP access control settings apply to the LAN interface only.
Enable IP Access Control
Enables access control based on IP source addresses.
Default policy
This option controls what to do with arriving IP packets that don’t match any of
the congured rules. They can be accepted or dropped.
IMPORTANT: If you set this to DROP and you have no ACCEPT rules congured,
access to the Web front-end over LAN is actually disabled. To enable access
again you can change the security settings via modem or ISDN dial in or by
temporarily disabling IP access control with the initial conguration procedure.
