Configuring VPN objects
134 Avaya VPNmanager Configuration Guide Release 3.7
IKE VPNs
Note:
Note: IKE VPNs are supported in VPNremote Client 3.0 and later.
An IKE VPN can run in certificate or preshared secret authentication mode. Also, IKE VPNs
always operate in tunnel mode, which means the entire original packet (header and payload) is
encrypted and inserted in the payload of an IPSec packet before it goes out to the public
networks.
Certificate mode involves the exchange of X.509 public-key certificates between endpoints of a
VPN tunnel to authenticate VPN tunnel end points. A certificate belonging to a specific endpoint
is authenticated by a third party certificate called an issuer’s certificate. Certificates can be
obtained from a third party Public Key Infrastructure (PKI). See for more information about using
a PKI. Certificate based VPNs cannot be manually rekeyed.
Preshared Secret mode involves the Diffie-Hellman algorithm for creating a shared secret key
that is used for authenticating VPN traffic. Large prime numbers and modular arithmetic
equations are exchanged between endpoints. Each endpoint uses the equations and numbers
to calculate the same shared secret key. The tunnel endpoints then use the shared secret key to
authenticate each other’s traffic. Even if the prime numbers and equations become publicly
known, the protocol still protects the shared secret key. As an added security measure,
preshared secret can be manually rekeyed at any time.
VPN packet processing modes
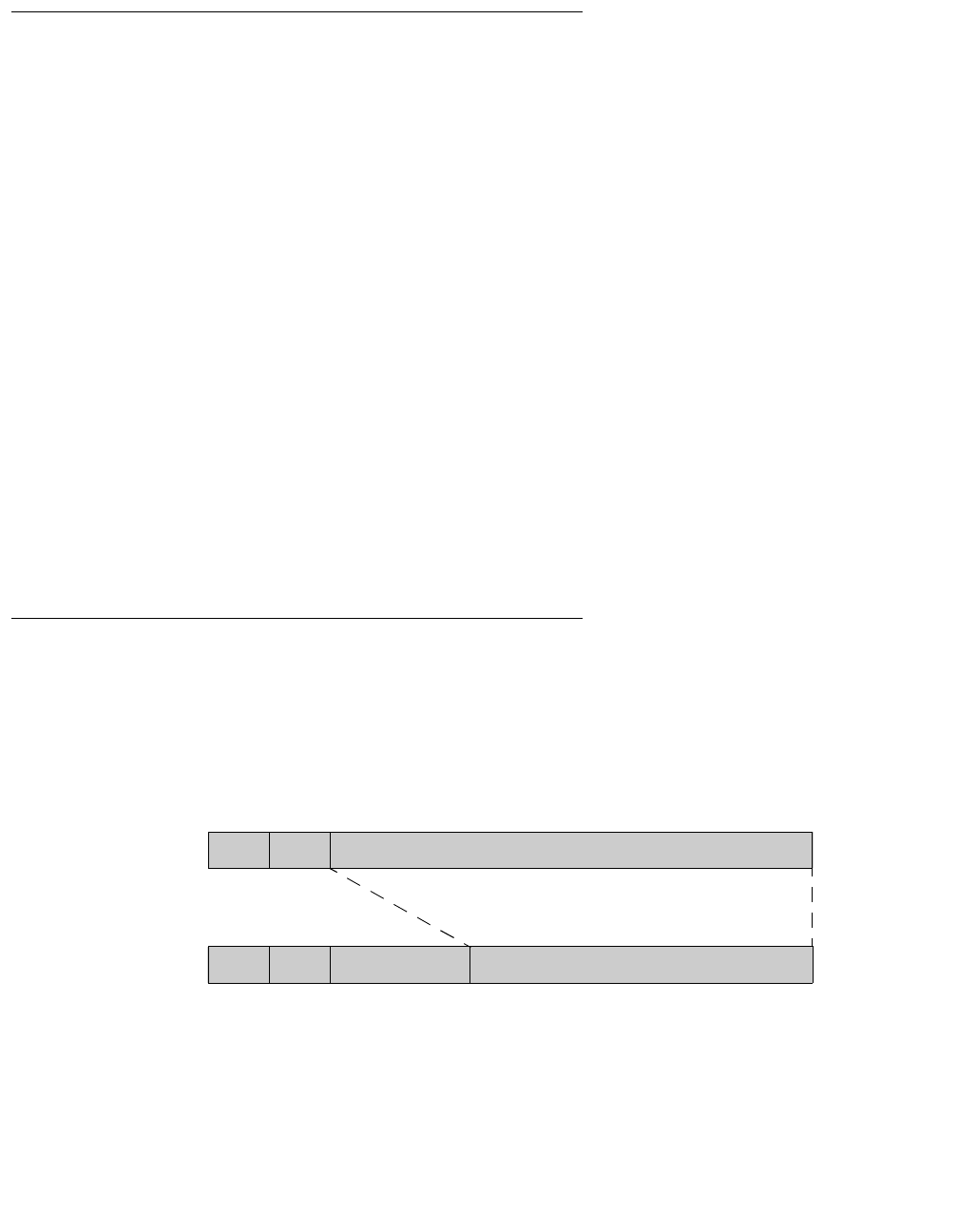
There are two ways to process packets when forming VPNs: transport mode and tunnel mode.
In transport mode, IP packets sent between VPN members are secured by applying VPN
services to the IP packet payload, leaving the original addressing header unchanged.
Source
Address
Dest.
Address
Payload
Source
Address
Dest.
Address
IPSec/SKIP
Overhead Payload with Applied VPN Services
Transport Mode
Secured VPN IP Packet
Original IP Packet


















