PROTECTION
TASK C
G3010B
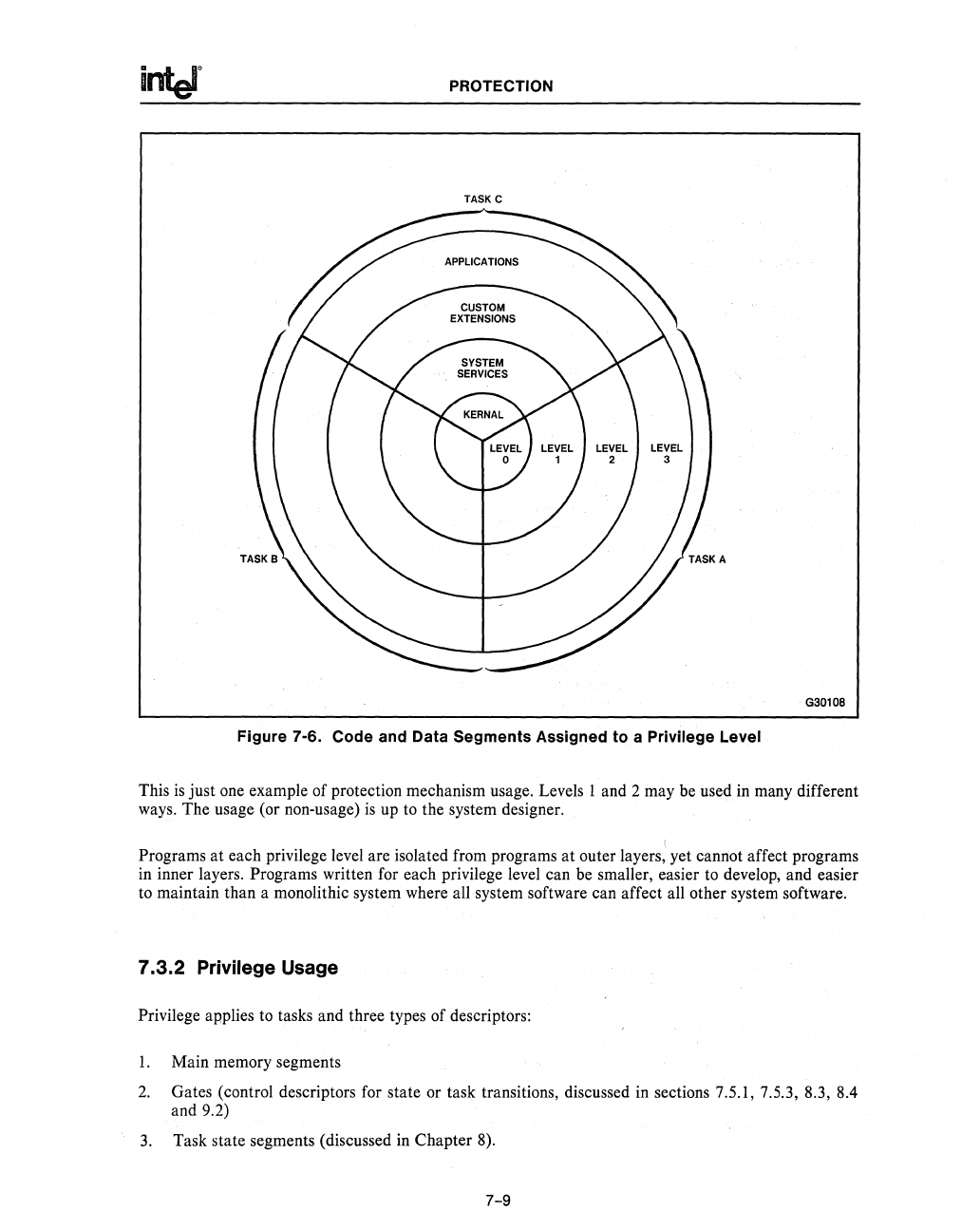
Figure 7-6. Code and Data Segments Assigned to a Privilege Level
This
is
just one example of protection mechanism usage. Levels 1 and 2 may be used in many different
ways. The usage (or non-usage)
is
up to the system designer.
Programs
at
each privilege level are isolated from programs
at
outer layers, yet cannot affect programs
in
inner layers. Programs written for each privilege level can be smaller, easier to develop, and easier
to maintain than a monolithic system where all system software can affect all other system software.
7.3.2 Privilege Usage
Privilege applies to tasks and three types of descriptors:
1.
Main memory segments
2.
Gates (control descriptors for state or task transitions, discussed in sections 7.5.1, 7.5.3, 8.3, 8.4
and 9.2)
3.
Task state segments (discussed in Chapter 8).
7-9


















