ADVANCED TOPICS
BASE + 10000H -"''"''''"''""'''1
STACK
SEG.B
BASE
+ 10000H -..------1
. STACK
SEG.B
+
~t~
~~~
-""*----1
NEW
BASE
-~,",,7777,",""
OLD
BASE
G3010a
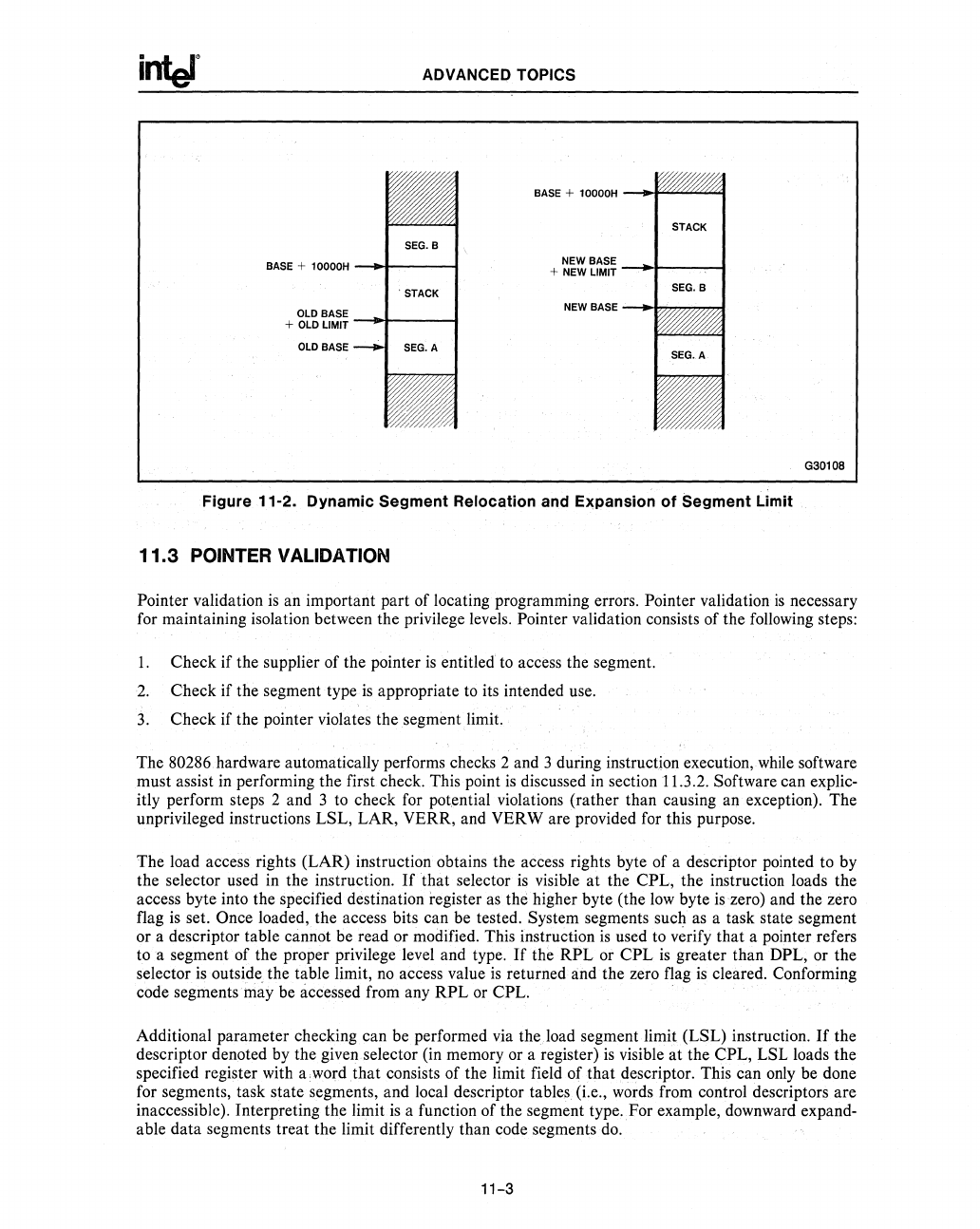
Figure 11-2. Dynamic Segment Relocation and Expansion of Segment
limit
11.3
POINTER VALIDATION
Pointer validation
is
an important part of locating programming errors. Pointer validation
is
necessary
for maintaining isolation between the privilege levels. Pointer validation consists of the following steps:
1.
Check if the supplier of the pointer
is
entitled to access the segment.
2.
Check if the segment type
is
appropriate to its intended use.
3.
Check if the pointer violates the segment limit.
The
80286 hardware automatically performs checks 2 and 3 during instruction execution, while software
must assist in performing the first check. This point
is
discussed in section 11.3.2. Software can explic-
itly perform steps 2 and 3
to
check for potential violations (rather than causing an exception). The
unprivileged instructions LSL, LAR, VERR, and VERW are provided for this purpose.
The load access rights (LAR) instruction obtains the access rights byte of a descriptor pointed to by
the selector used in the instruction.
If
that selector
is
visible at the CPL, the instruction loads the
access byte into the specified destination register
as
the higher byte (the
low
byte
is
zero) and the zero
flag
is
set. Once loaded, the access bits can be tested. System segments such
as
a task state segment
or a descriptor table cannot be read or modified. This instruction
is
used to verify that a pointer refers
toa
segment of the proper privilege level and type.
If
the RPL or CPL
is
greater than DPL, or the
selector
is
outside. the table limit,
no
access value
is
returned and the zero flag
is
cleared. Conforming
code segmentSinay be accessed from any
RPL
or CPL.
Additional parameter checking can be performed via the load segment limit (LSL) instruction.
If
the
descriptor denoted by the given selector (in memory or a register)
is
visible at the CPL, LSL loads the
specified register with a .word
that
consists of the limit field of that descriptor. This can
only
be done
for segments, task state segments, and local descriptor tables (i.e., words from control descriptors are
inaccessiblc). Interpreting the limit
is
a function of the segment type.
For
example, downward expand-
able data segments treat the limit differently than code segments do.
11-3


















