ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual
5-36 Virtual Private Networking
v1.1, August 2010
2. Configure the following fields:
• Name. Enter a descriptive name that will identify this certificate.
• Subject. This is the name which other organizations will see as the holder (owner) of the
certificate. Since this name will be seen by other organizations, you should use your
registered business name or official company name. (Using the same name, or a derivation
of the name, in the Title field would be useful.)
3. From the pull-down menus, choose the following values:
• Hash Algorithm: MD5 or SHA2.
• Signature Algorithm: RSA.
• Signature Key Length: 512, 1024, 2048. (Larger key sizes may improve security, but may
also decrease performance.)
4. Complete the optional fields, if desired, with the following information:
• IP Address. If you have a fixed IP address, you may enter it here. Otherwise, you should
leave this field blank.
• Domain Name. If you have an Internet domain name, you can enter it here. Otherwise,
you should leave this field blank.
• E-mail Address. Enter the email address of a technical contact in your organization.
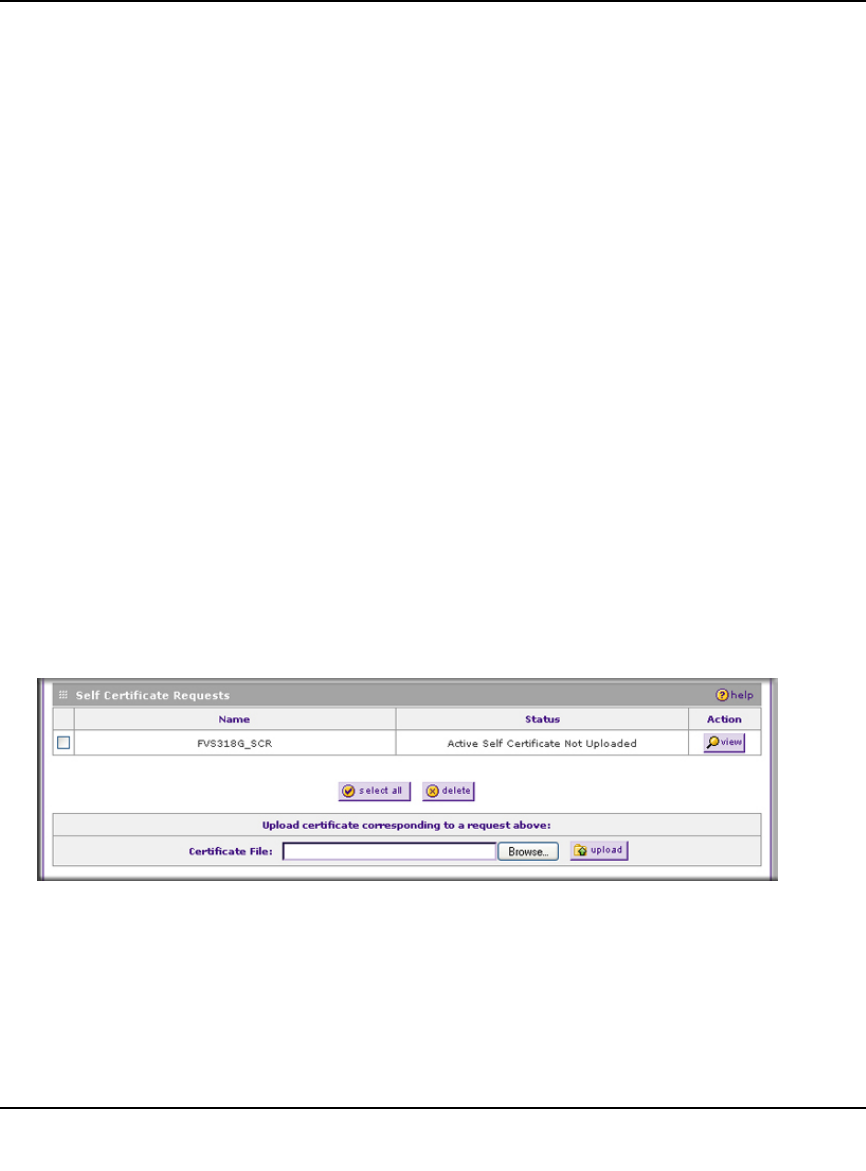
5. Click Generate. A new certificate request is created and added to the Self Certificate
Requests table.
Figure 5-26
