Connection Policy Window 6-7
FDDI Applications
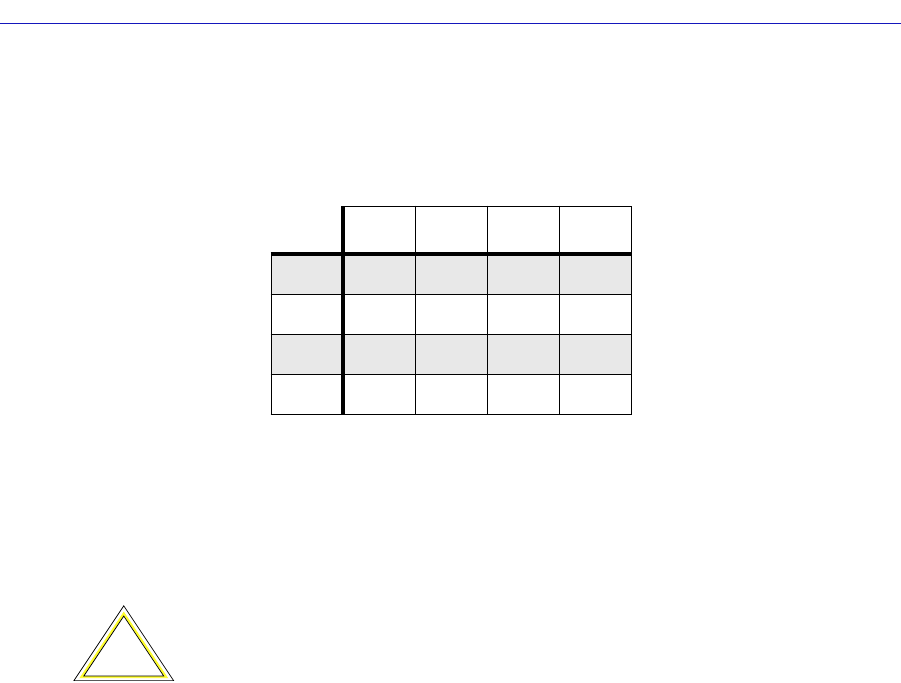
The following table summarizes the FDDI connection rules:
V — valid connection
X — illegal connection
U — undesirable (but legal) connection
P — valid, but when both A and B are connected to M ports (a dual-homing
configuration), only the B connection is used.
Each device has its own connection policy; however, when two devices attempt to
connect, their combined established connection policies dictate the connections
that will be allowed. In an attempted connection between two nodes, the most
lenient policy will determine whether the connection (as long as it is legal) can be
made. For example, if two FDDI nodes attempt an AÑ>A connection, and this
connection is not allowed at one FDDI node but allowed at the other, the
connection would be accepted. If the connection policy at both nodes disallows
the connection, the connection will be rejected.
This is a read-only window; you currently cannot edit the HSIM-F6Õs connection
policy directly from this window.
Table 6-1. FDDI Connection Rules
ABSM
A V, U V V, U V, P
B V V, U V, U V, P
S V, U V, U V V
MVVVX
!
CAUTION
Though technically legal under FDDI connection rules, undesirable connections will
cause a twisted or wrapped ring.


















