9-7
Catalyst 2950 and Catalyst 2955 Switch Software Configuration Guide
OL-10101-02
Chapter 9 Configuring IEEE 802.1x Port-Based Authentication
Understanding IEEE 802.1x Port-Based Authentication
For more information about AV pairs, see RFC 3580, “IEEE 802.1X Remote Authentication Dial In User
Service (RADIUS) Usage Guidelines.”
Using IEEE 802.1x Authentication with VLAN Assignment
You can limit network access for certain users by using VLAN assignment. After successful
IEEE
802.1x authentication of a port, the RADIUS server sends the VLAN assignment to configure the
switch port. The RADIUS server database maintains the username-to-VLAN mappings, assigning the
VLAN based on the username of the client connected to the switch port.
When configured on the switch and the RADIUS server, IEEE 802.1x authentication with VLAN
assignment has these characteristics:
• If no VLAN is supplied by the RADIUS server or if IEEE 802.1x authentication is disabled, the port
is configured in its access VLAN after successful authentication.
• If IEEE 802.1x authentication is enabled but the VLAN information from the RADIUS server is not
valid, the port returns to the unauthorized state and remains in the configured access VLAN. This
prevents ports from appearing unexpectedly in an inappropriate VLAN because of a configuration
error.
Configuration errors could include specifying a malformed VLAN ID, a nonexistent VLAN ID, or
attempted assignment to a voice VLAN ID.
• If IEEE 802.1x authentication is enabled and all information from the RADIUS server is valid, the
port is placed in the specified VLAN after authentication.
• If the multiple-hosts mode is enabled on an IEEE 802.1x port, all hosts are placed in the same VLAN
(specified by the RADIUS server) as the first authenticated host.
• If IEEE 802.1x authentication and port security are enabled on a port, the port is placed in the
RADIUS-server assigned VLAN.
• If IEEE 802.1x authentication is disabled on the port, it is returned to the configured access VLAN.
When the port is in the force authorized, force unauthorized, unauthorized, or shutdown state, it is placed
in the configured access VLAN.
If an IEEE 802.1x port is authenticated and put in the RADIUS-server assigned VLAN, any change to
the port access VLAN configuration does not take effect.
The IEEE 802.1x authentication with VLAN assignment feature is not supported on trunk ports, dynamic
ports, or with dynamic-access port assignment through a VLAN Membership Policy Server (VMPS).
To configure VLAN assignment you need to perform these tasks:
• Enable authentication, authorization, and accounting (AAA) authorization.
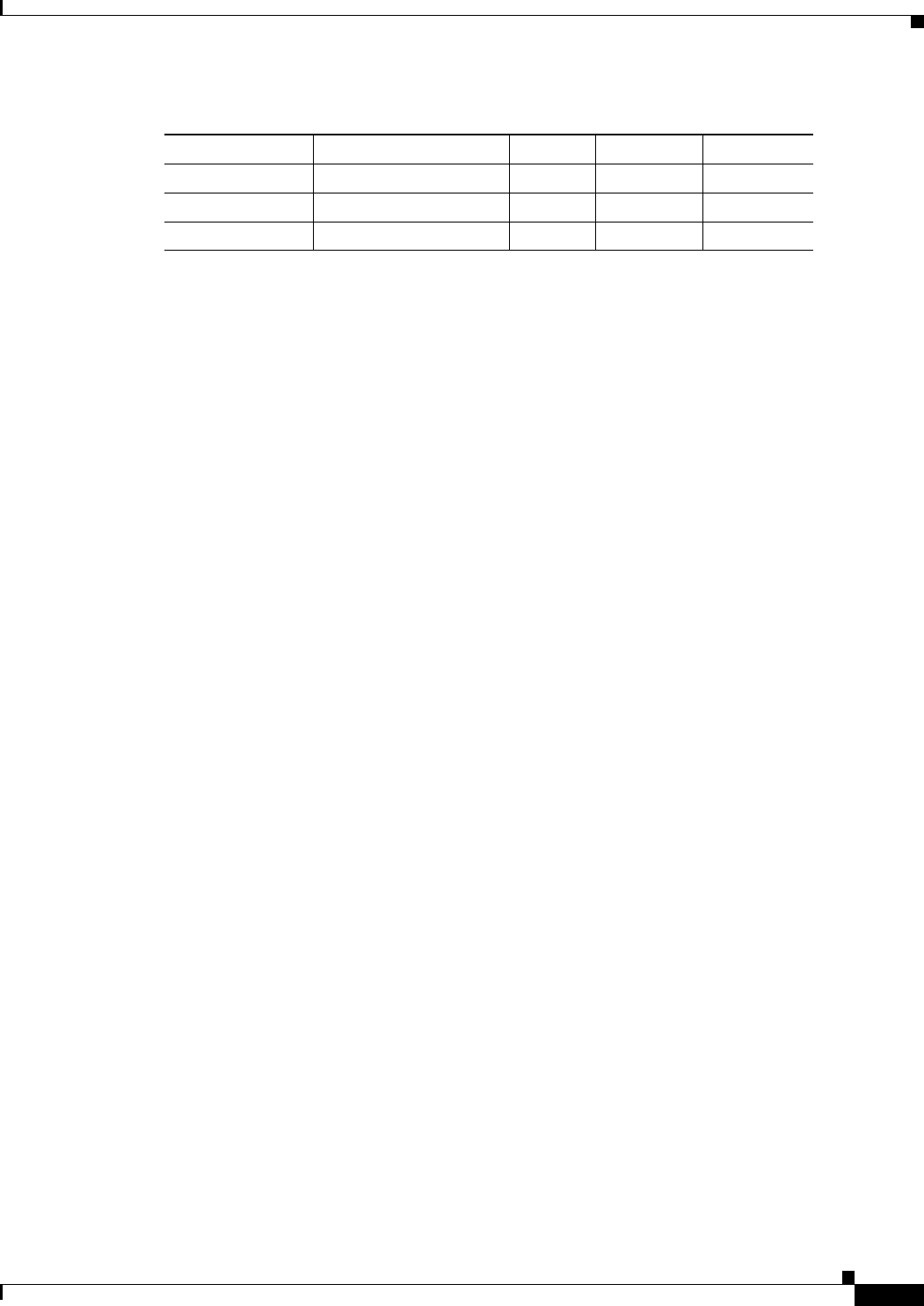
Attribute[46] Acct-Session-Time Never Never Always
Attribute[49] Acct-Terminate-Cause Never Never Always
Attribute[61] NAS-Port-Type Always Always Always
1. The Framed-IP-Address AV pair is sent only if a valid Dynamic Host Control Protocol (DHCP) binding
exists for the host in the DHCP snooping bindings table.
Table 9-1 Accounting AV Pairs (continued)
Attribute Number AV Pair Name START INTERIM STOP


















