̈ Chapter 8: Firewall LANCOM Reference Manual LCOS 3.50
159
Firewall
Sorting is done according to address, protocol and port. The table contains the
following elements:
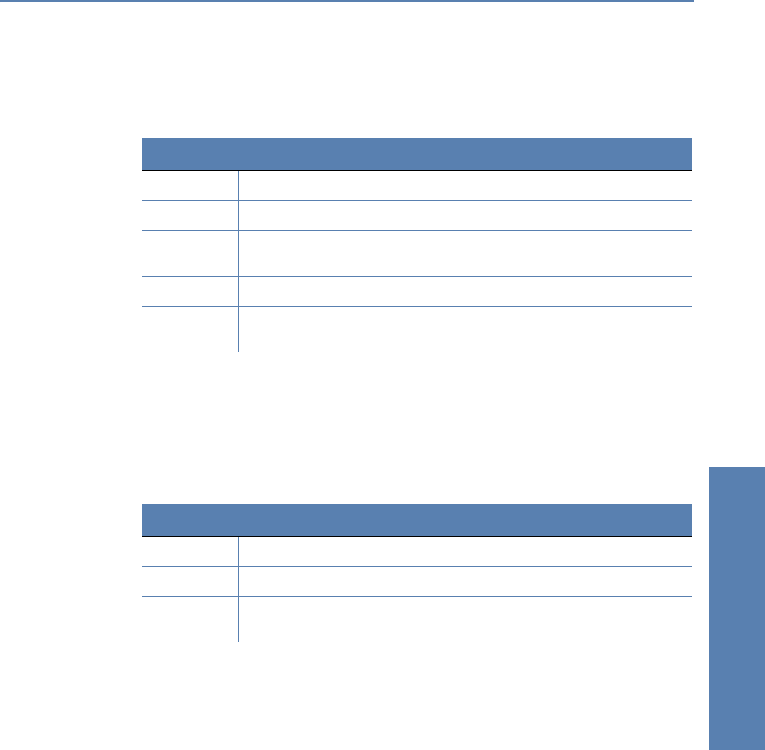
Host block list
The address of a station is filed in the host block list, if blocking of the sender
was selected in a filter’s packet action. This table is a sender address sorted
semi-dynamic table and contains the following elements:
8.3.10 Firewall limitations
Apart from understanding the functioning of Firewalls, it is also very impor-
tant to discern their limitations and to extend them if necessary. The Firewall
does not protect against malicious contents coming through the permitted
ways into your local network. It is true that certain effects of some viruses and
worms are stopped, because communication is blocked via the required ports,
but no Firewall alone is a comprehensive protection against viruses.
Also monitoring of sensitive data in the Internet is not be prevented by a Fire-
wall. If data once reaches the unsecured net beyond the Firewall, then it is
exposed to well-known dangers. Despite using a Firewall, any confidential
information such as contracts, passwords, development information etc.
should be transmitted only over protected connections, i.e. by using suitable
data encryption and VPN connections.
Element Element meaning
Address Address of the station, to which the blocking should apply.
Protocol Used protocol (TCP/UDP etc.) The protocol is decimally indicated.
Port Port to close at the station. If the respective protocol is not port related, then
the entire protocol for this station becomes closed.
Timeout Duration of the blocking in minutes.
Filter rule Name of the rule, which has produced the entry (determines also the actions
to be executed), when a suitable packet is received.
Element Element meaning
Address Address of the station, to which the blocking should apply.
Timeout Duration of the blocking in minutes.
Filter rule Name of the rule, which has generated the entry (determines also the
actions to be executed), when a suitable packet is received.


















