LANCOM Reference Manual LCOS 3.50 ̈ Chapter 11: Wireless LAN – WLAN
224
Wireless LAN – WLAN
̈ A simplified procedure for deriving the Master Secret mentioned in the
last section, which can be performed without a RADIUS server.
̈ Negotiation of encryption procedure between access point and client.
TKIP
TKIP stands for Temporal Key Integrity Protocol. As the name suggests, it
involves an intermediate solution for temporary use until a truly strong
encryption procedure is introduced, but which deals with the problems of
WEP, never the less. One design requirement was therefore that the new
encryption procedure should be implementable on existing WEP/RC4
hardware with a reasonable effort. When TKIP was defined, it was already
foreseeable that it would be used well into the era of 54/108Mbit LANs, and
a purely software-based encryption would be associated with too high a
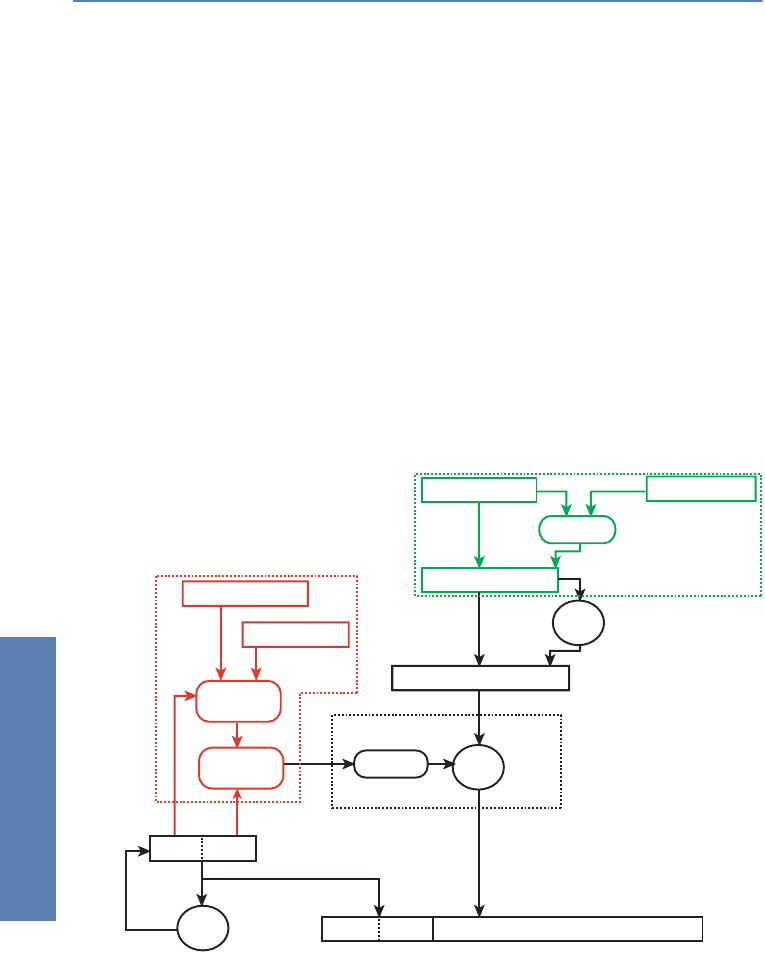
speed penalty on most systems. In the 'block diagram' of TKIP (Figure 3),
therefore, there are many components of WEP to be seen, which generally
exist in hardware in WEP cards and thus can effectively be used for TKIP.
As components already familiar from WEP, one recognises the RC4 engine
used for the actual encryption and decryption, as well as the CRC module. As
Figure 3: Procedure for TKIP/Michael
Data
Data + Michael + CRC
CRC
Key mixing
(phase 1)
IVHi
+1
Generator
XOR
RC4
Michael key
Michael
Data + Michael
Source MAC address
TKIP key
Key mixing
(phase 2)
IVLo
Data + Michael + CRC (encrypted)
IVHi IVLo
TKIP
Michael


















