LANCOM Reference Manual LCOS 3.50 ̈ Chapter 14: Virtual Private Networks—VPN
332
Virtual Private Networks—
VPN
The result is a nominal key length of 168 bit, with an effective key length
of 112 bits.
Triple-DES combines the sophisticated DES technology with a suffi-
ciently long key and is therefore considered to be highly secure. Triple-DES
is slower than other processes, however.
̈ Blowfish
This development by the renowned cryptographer Bruce Schneier is a
symmetrical encryption process. Blowfish achieves outstanding data
throughput on multifunction processors. The process is reputed to be
extremely efficient and secure.
̈ CAST (from the authors Carlisle Adams und Stafford Tavares)
is a symmetrical process with a key length of 128 bits. CAST permits the
modification of parts of the algorithm at runtime.
The encryption settings can be modified in the expert configuration
within LANconfig. Modifications of this sort are generally only
required when setting up VPN connections between devices from
different manufacturers. LANCOM gateways offer the encryption as
standard either after AES (128 bit), Blowfish (128 bit) or Triple-DES
(168 bit).
14.8.4 Authentication – the AH protocol
The AH protocol (Authentification Header) guarantees the integrity and
authenticity of the data. Integrity is frequently regarded as a component of
authenticity. In the following, we will consider integrity to be a separate
problem that is resolved by AH. In addition to integrity and authenticity, AH
also provides effective protection against the replay of received packets
(Replay Protection).
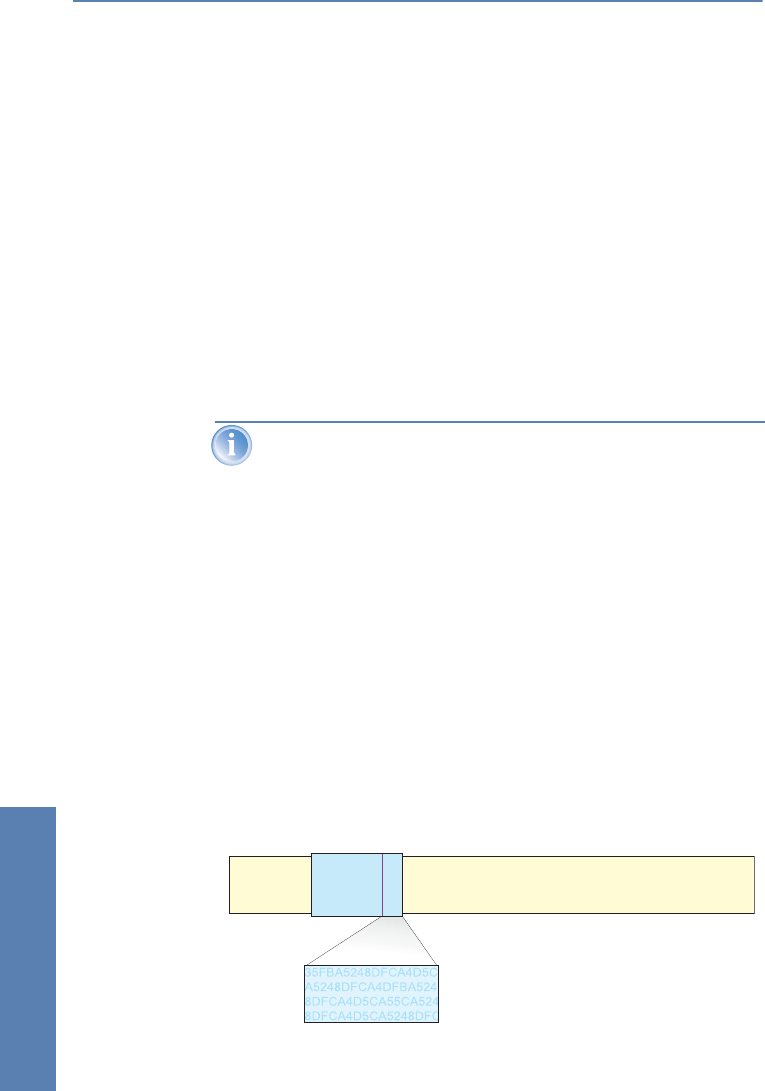
AH adds its own header to IP packets immediately after the original IP header.
The most important part of this AH header is a field containing authentication
data, often referred to as the Integrity Check Value (ICV).
IP header
AH header Data
Authentication data,
ICV


















